What is Identity Governance and Administration?
What is IGA?
Identity Governance and Administration (IGA) is a branch of Identity and Access Management (IAM) that refers to the security processes that govern and manage identities within an organization. A vital piece of today’s cybersecurity tech stack, IGA secures digital identities (human or machine), and automates application and data access so security teams can streamline processes, ensure compliance and reduce organizational risk. These solutions enable a host of functions including application and employee access provisioning, access reviews, role-based access, employee/contractor onboarding, lifecycle management, and tasks surrounding the separation of duties (SOD).
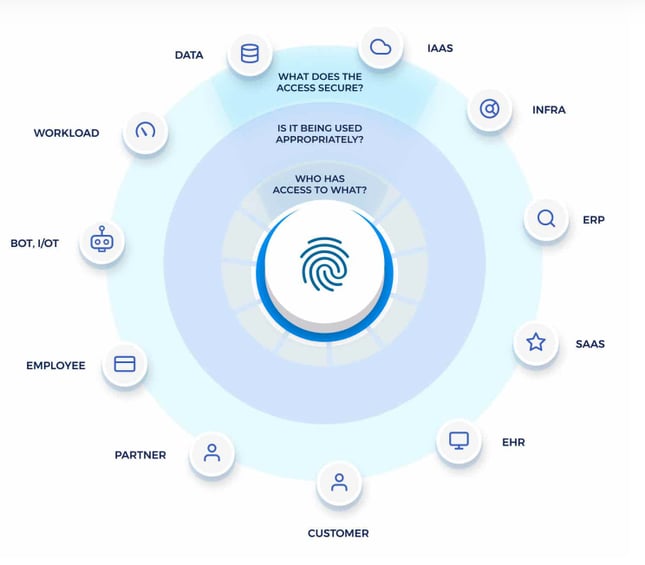
Identity Governance and Administration (IGA) in the Workplace
Why do companies need identity governance and administration? In short, ongoing business transformation initiatives and remote work have changed the cybersecurity landscape, and identity has become the new security perimeter. As companies undergo digital transformation, it often becomes a catalyst for organizations to modernize their identity governance programs. Remote workers and reliance on third-party vendors and contractors is the new normal, but they introduce security risks. Meanwhile, IT ecosystems continue to grow with skyrocketing numbers of silicon identities (bots, loT, workloads) that expand the attack surface, while privacy regulations continue to evolve.
Identity governance and administration helps companies embrace the benefits of digital transformation and achieve regulatory compliance while ensuring that only the right people (or machines) have access to the right things at exactly the right time. When done right, IGA increases organization efficiency, improves security posture, and provides valuable insights about employee activity and needs.
IGA has become a foundational cybersecurity strategy for information security professionals because it provides a framework for companies to reduce risk and achieve compliance. It’s an area that provides operational management, integration, security, customization, and overall support for an enterprise IAM program.
IGA brings together entitlement discovery, the decision-making process, and access review and certification with identity lifecycle and user provisioning. Inappropriate and outdated access to company resources is common across many enterprise IAM programs today, creating substantial risk. Comprehensive IGA programs can help identify and manage these risks and address compliance requirements.
Benefits of Identity Governance and Administration (IGA) and Business Impact
IGA solutions are a core component of a successful cybersecurity program with numerous business benefits. Benefits of Identity Governance and Administration include lower operational costs, increased IT efficiency, compliance management, and overall risk reduction.
Identity Governance and Administration Lowers Operational Costs
Automating functions such as application provisioning, entitlement reviews and approvals, onboarding, and lifecycle management provides increased accuracy and promotes workflow efficiencies, productivity gains, and an improved security posture. Automating routine, manual, and time-consuming processes can significantly lower costs and allow personnel to focus on more significant projects or enhancements.
Identity Governance and Administration Reduces Risk & Improves Security Posture
Based on the premise of least privilege, IGA helps organizations meet Zero Trust security objectives, can provide visibility across all identities, human and machine, and help make risk-based decisions. They can help analyze usage and identify risky activities across all identities and environments. Automation reduces the risk of mistakes caused by manual processes that could result in increased risk due to such things as overprovisioning, undetected orphaned accounts, improper certification of access requests and changes, and separation of duty violations.
Achieve Continuous Compliance with Identity Governance and Administration
The regulatory landscape continues to become more difficult to manage. IGA helps organizations quickly and effectively validate compliance or identify gaps needing remediation. Quality reporting easily provides auditors the information they need to verify compliance or show that needed remediation actions have been completed.
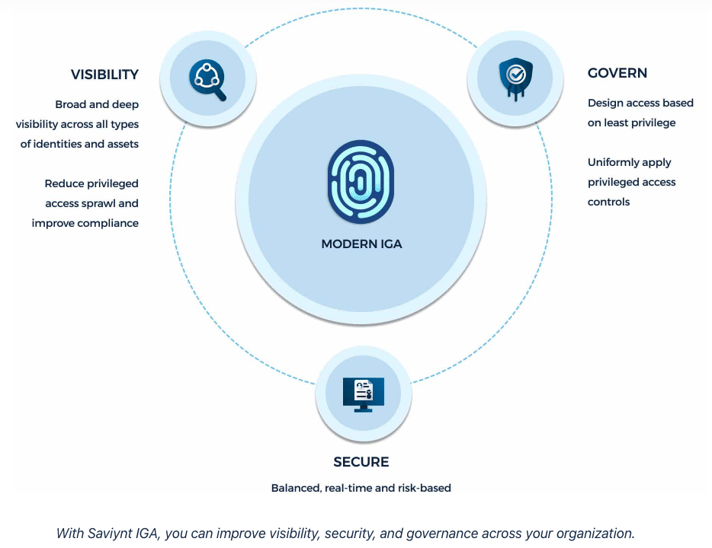
Saviynt Identity Governance and Administration (IGA)
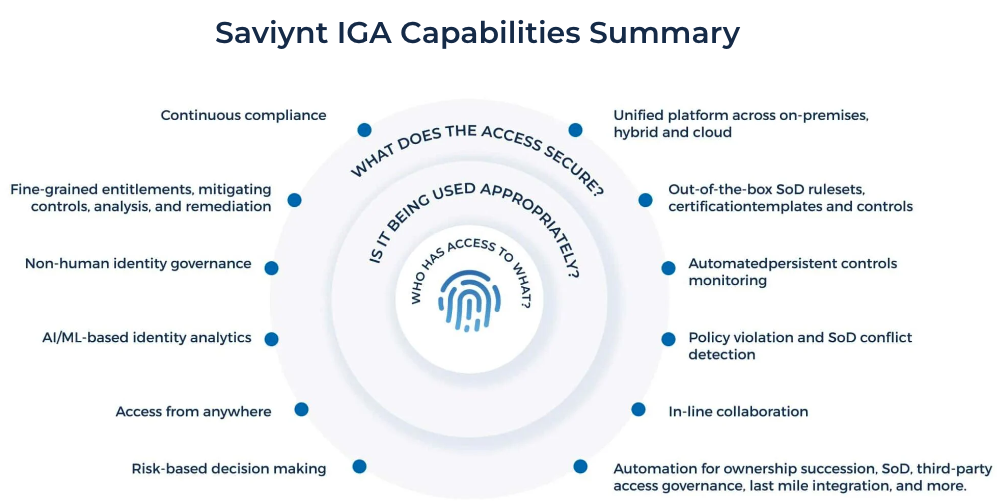
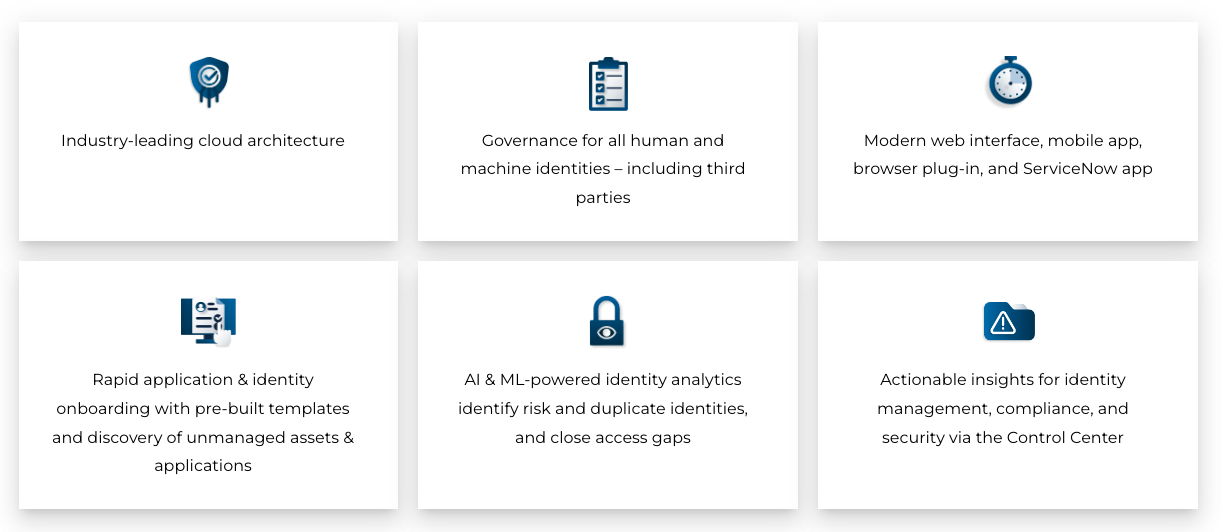
Powered by a comprehensive identity warehouse and user experience to drive frictionless access, Saviynt Identity Governance and Administration (IGA) enables Zero Trust in your hybrid and multi-cloud environment by providing the following features:
How does Saviynt’s IGA solution affect your bottom line? Forrester’s Total Economic Impact™ (TEI) study examines the return on investment (ROI) organizations realize with the Saviynt Enterprise Identity Cloud. In this commissioned study, Forrester estimates that implementing Saviynt can save your organization $34.4M and achieve a 240% ROI over three years.
Learn more about The Identity Cloud here.
Resources


