What is Zero Trust Security?
What is Zero Trust Security?
Zero Trust Security is a cybersecurity model that moves beyond an implicit trust model and continuously re-evaluates risk and trust levels of every digital interaction. It is based on the principle of “never trust, always verify” and provides the “least access” required to relevant data, applications, and assets as they are needed to complete a job.
Zero Trust is designed to accelerate digital transformation and protect remote workforces and modern IT environments through strong authentication policies and granular access controls, preventing lateral movement across systems.
What is Zero Trust Identity?
Zero Trust Identity is the practical application of identity to support and strengthen Zero Trust principles. This approach requires delivering more robust security without negatively impacting productivity or business agility.
The identity layer is an essential part of an effective Zero Trust strategy. This approach has three key pillars:
- A shift in organizational mindset
- A shift in strategy away from a point solution approach
- A shift towards a new identity-based architecture
What Does a Zero Trust Approach Look Like?
Making the move to Zero Trust requires significant long-term investment. This includes deploying identity-aware security solutions, implementing the right policies and business processes, and educating stakeholders to understand the importance of the Zero Trust mindset. And ultimately, it will entail re-architecting IT environments and applications so that they’re wholly suited for — and can fully benefit from — cloud computing.
Depending on your current security architecture, technology environment, and business needs, you’ll need to develop your own unique Zero Trust strategy, one that’s personalized in its timeline and approach.
How to Develop a Zero Trust Strategy
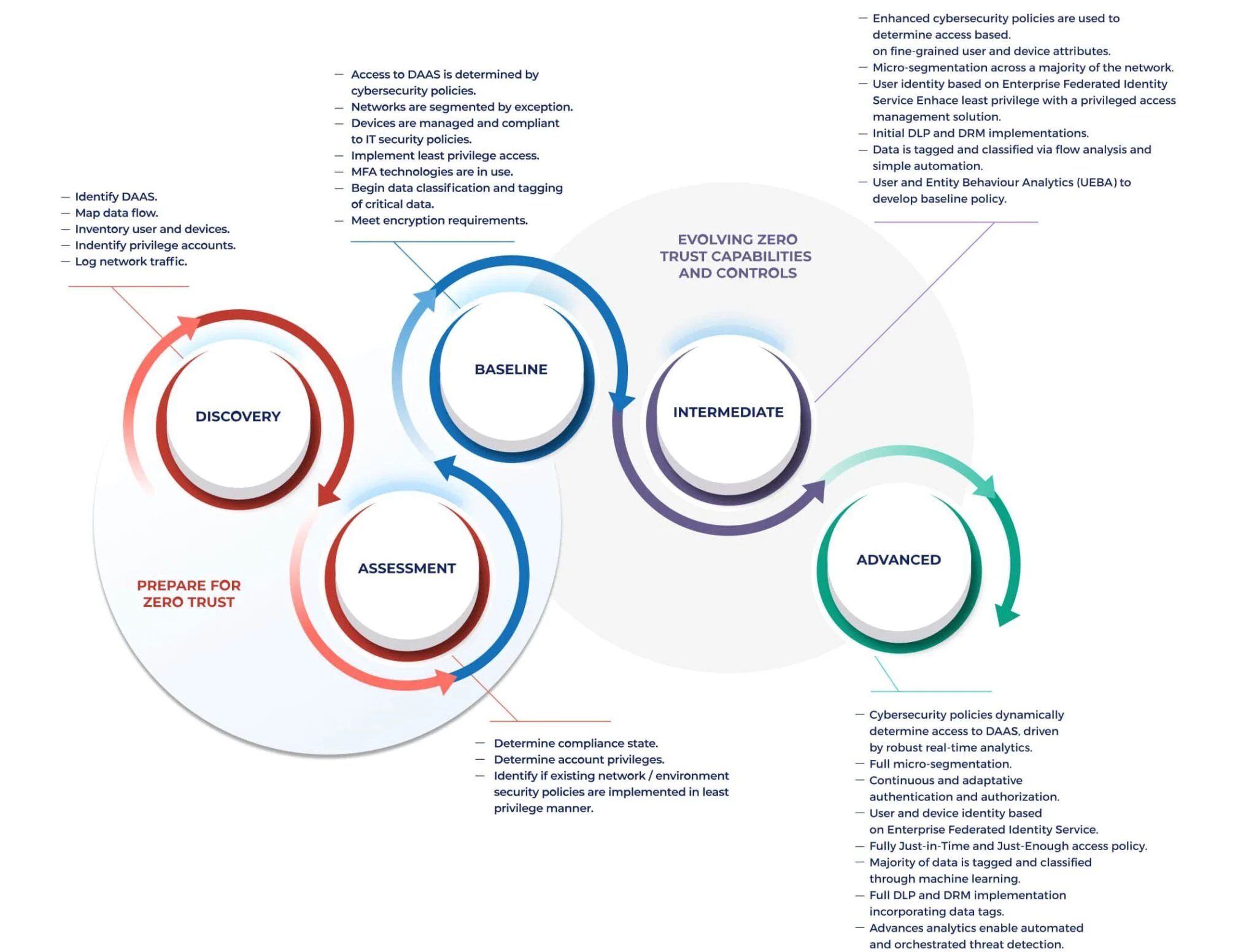
So how do you move toward Zero Trust Identity? The first step is to begin with an assessment. You need to understand your asset universe and where sensitive data resides. You’ll need to begin by gaining a thorough understanding of the IT asset and identity ecosystem that spans your organization. Where do mission-critical, sensitive, and regulated data reside? Then, determine who has access to those assets. Among those users, how many have elevated privileges? Are these standing privileges?
Next, you’ll want to focus on how access policies are administered and enforced. The least mature organizations are those that configure access and assign attributes manually that enforce static security policies, and that lack integrated access governance and privileged access management capabilities as well as cross-organizational visibility. Organizations that are beginning to centralize visibility, identity management, and policy enforcement will be further along the road to Zero Trust, particularly as they become better able to enforce least privilege access automatically.
Once you’ve centralized policy administration and enforcement, the next step is clean-up. Conducting an organization-wide analysis to determine where there is excessive access will enable you to limit and ultimately remove it. How many (if any) of your existing security policies are implemented in a least privilege manner?
Reaching Zero Trust Maturity
Once you’ve developed a Zero Trust strategy, we suggest that organizations seeking to increase their maturity follow the recommendations for evolving Zero Trust capabilities and controls outlined in the Maturity Model developed by the U.S. Department of Defense (DoD). These are published in the DoD’s Zero Trust Reference Architecture. This model establishes three levels of Zero Trust maturity, and organizations can advance from one to the next by implementing additional capabilities and controls.
How to Build a Zero Trust Identity Architecture
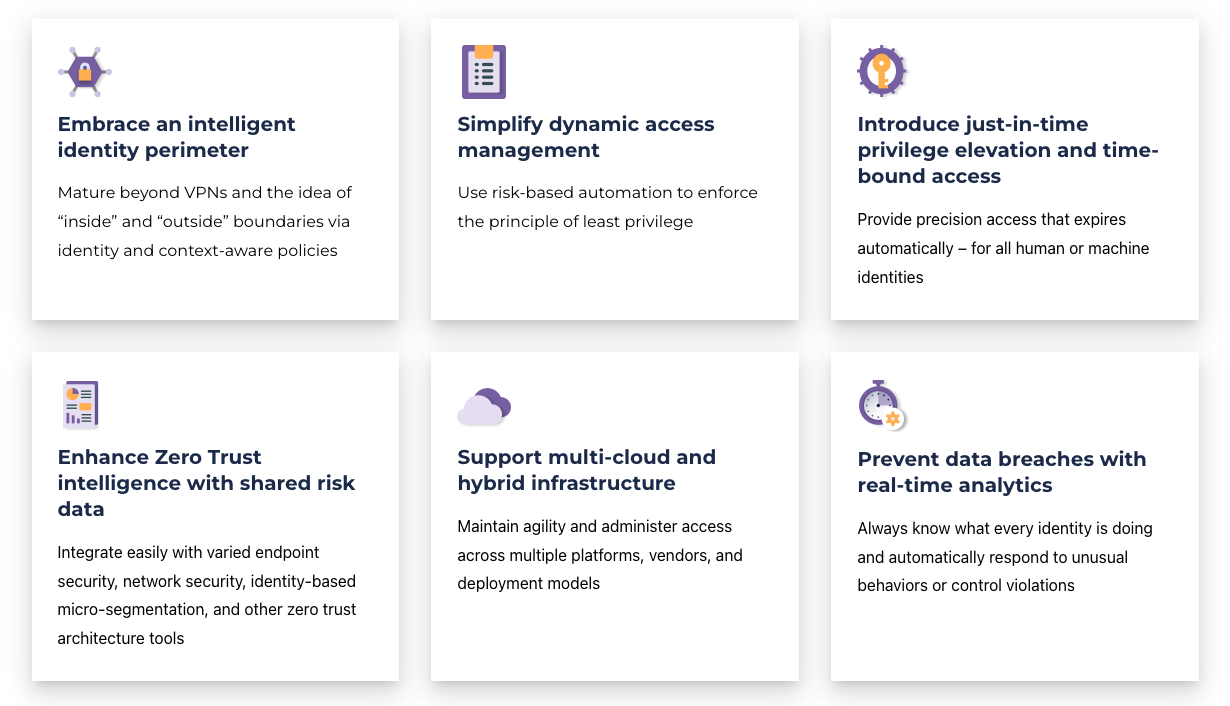
Refactoring your security architecture to support modern cloud-based technologies requires a modern identity solution that integrates with existing security and compliance tools. This way, a Zero Trust Identity Architecture can continue to enforce existing use cases while enabling the creation of new ones. Achieving this requires architecture built upon interoperable solutions that can readily exchange information. This will also enable your organization to make use of visibility, risk, and threat intelligence to drive automated decision-making.
In the wake of several high-profile cyber attacks and breaches involving federal agencies, the National Institute of Standards and Technologies (NIST) created an abstract definition of a Zero Trust Architecture along with several deployment models. Elaborated in NIST SP 800-207, Zero Trust Architecture, this model is explicitly intended to provide a roadmap for enterprise security architects looking to implement Zero Trust-based approaches to information security.
According to the NIST model, a Zero Trust Architecture must incorporate three core components. These are:
- A policy engine, decides to grant, deny, or revoke access to resources for all entities that request to do so. The policy engine calculates trust scores or confidence levels to serve as a basis for each of these decisions.
- A policy administrator, establishes and terminates the connection between an entity and a resource. The policy administrator relies on decisions made by the policy engine to determine whether to allow individual sessions to proceed. It generates authentication tokens or credentials for each session.
- A policy enforcement point, which enables and monitors ongoing connections between entities and enterprise resources.
.webp?width=1535&height=918&name=zero-trust-architecture@2x%20(1).webp)
With Zero Trust architecture, all interactions are to be achieved in the most secure manner possible, emphasizing consistent identity verification and authentication. And all interactions are continuously reassessed. Each time access to a resource is granted, this is done for only one session — and for that resource alone. Every access request is evaluated dynamically based on organizational policy and risk evaluation. Each request is checked to ensure that the identity-making the request (user or machine identity) should be granted access, that their laptop, mobile device, or other IT system is behaving appropriately, and that the requested resource has the right characteristics.
To obtain the complete set of capabilities needed to achieve holistic visibility and control, you’ll need multiple solutions with overlapping and tightly integrated capabilities.
.jpg?width=2048&height=966&name=zero-trust-architecture-2@2x-2048x966%20(1).jpg)
Building a Zero Trust architecture isn’t a simple, one-step process. It instead requires implementing new solutions that can gather intelligence across your IT ecosystem and inform the SASE, access management, and security tools that enforce policies. Designing such an architecture means thinking differently about interconnectivity and the value of an open, standards-based approach. It means thinking smarter in your entire approach to identity and security across your organization.
Dive into the details by reading more about the Building Blocks of Zero Trust Identity Architecture on our blog.
What are the Benefits of Zero Trust?
-
Gain Greater Visibility Across the Enterprise
Because Zero Trust never assumes anyone or anything is trusted, you decide what resources and activities you’ll need to cover in your security strategy. Ideally, all data and computing sources are protected.
-
Simplify IT Management
Because Zero Trust rests on the foundation of continual monitoring and analytics, you can use automation to evaluate access requests. Access is automatically granted if the privileged access management (PAM) system judges the request to be standard, or a low risk, based on key identifiers. IT doesn’t need to be involved in approving every access request — they serve in an admin capacity only when the automated system flags requests as suspicious.
-
Gain Insights and Work Smarter
Zero Trust also enables your security team to work smarter. Because it utilizes centralized monitoring, you can easily generate reliable data stored in a single location. This facilitates robust analytics, so your team can gain insights they wouldn’t be able to otherwise. As a result, your security team can maintain a more secure environment.
-
Improve Data Protection
Zero Trust delivers better data protection, as a Zero Standing Privilege framework combined with just-in-time (JIT) access prevents rogue employees or malware from gaining access to large portions of your network due to the elimination or reduction of standing access.
-
Secure Your Remote Workforce
With Zero Trust, identity is the perimeter. Firewalls are no longer sufficient now that users are spread across the world, and data is spread across the cloud. Identity is attached to the users, devices, and applications seeking access, so adopting a Zero Trust approach offers robust protection for workers and data in any location.
With identity as the perimeter, founded on time-limited access and just enough access, Zero Trust enables remote security. Old credentials are no longer floating around. People cannot access data or resources they shouldn’t after moving to a different department — or organization. And everyone can work more efficiently because slow-moving VPN tunnels don’t bog them down. Additionally, identity allows us to assume that even employees, resources, and infrastructure inside the organization could be compromised.
-
Streamline User Access
Organizations that are beginning to centralize visibility, identity management, and policy enforcement will be further along the road to Zero Trust, particularly as they become better able to enforce least privilege access automatically. Automation that accompanies a Zero Trust framework enables users to access what they need quickly, so they don’t have to wait on administrators for approval.
One approach is to refactor your security architecture to support modern cloud-based technologies. This requires a modern identity solution that integrates with existing security and compliance tools. This way, a Zero Trust Identity Architecture can continue to enforce existing use cases while enabling the creation of new ones. Achieving this requires architecture built upon interoperable solutions that can readily exchange information. This will enable your organization to make use of visibility, risk, and threat intelligence to drive automated decision-making.
-
Continuous Compliance
Zero Trust helps to ensure continuous compliance with every access request being evaluated and logged. Tracking each access request’s time, location, and applications creates a seamless audit trail. With continuous compliance, audits are streamlined as there is a contiguous chain of evidence for all access requests. This minimizes the effort required to produce evidence, making upholding governance faster and more efficient.
Want to learn more about the seven primary benefits of Zero Trust? Check out our post to gain a deeper understanding.
Saviynt & Zero Trust
Saviynt cloud identity & access governance strengthens your Zero Trust strategy. Our Zero Trust toolkit includes identity governance and administration, privileged access management, application access governance, third-party access governance, and data access governance products.
Ready to make Zero Trust the foundation of your security?
Questions People Often Ask About Zero Trust
With a Zero Trust model, will employees have the impression that they aren’t trusted or won’t have access to information they need?
No. Zero Trust supports teamwork and the sharing of information, though it ensures that data access takes place on a need-to-know basis, where information is shared only after verifying the appropriateness of the access request. Just because there’s no assumed or implied trust doesn’t mean there’s no trust. Instead, there’s explicitly justified and appropriately granted trust. Also, access is continually validated to ensure that it remains appropriate throughout the session and the whole of an identity’s lifecycle.
Is it too difficult or impractical to implement Zero Trust in my organization?
No, you can implement Zero Trust in stages. Zero Trust adoption is an iterative journey, not a destination. Successful adoption requires you to take the right strategy as you progress. The Zero Trust journey includes multiple components, ranging from security awareness training to multiple layers within a defense-in-depth approach that’s grounded in the understanding that identity is the new perimeter. Whenever you grant access to a resource, you incur some degree of risk. Zero Trust doesn’t eliminate this risk, but it does involve the continuous improvement of security processes so as to mitigate it. Improving your ability to monitor assets and access usage in order to eliminate unnecessary access rights should be done gradually and incrementally.
Are tech companies the only organizations that should consider adopting Zero Trust?
No. In our digital world dominated by data, dependent on cloud computing, connected by mobile devices, and rife with IoT, every company has become a tech company. Realizing and acknowledging this demands a mindset shift. You must view the world through a different lens. This applies to larger global enterprises and smaller businesses alike. You have to accept that technology is at the core of every business. Whether companies host their own hardware or rely on SaaS solutions, nearly every core business function — from HR to accounting and sales — relies on technology. Which is why both organizational assets and sensitive data exist within every corner of IT systems. These resources must not only be secured but also aggressively monitored and actively protected.
Should one assume that all internal identities and resources are typically safe?
No. A Zero Trust mindset requires that the assumption that internal identities and resources are safe to be abandoned. The new assumption must be that every identity and access request is suspect and must be validated. Moving to this mindset advances your organization from a reactive stance on security to a proactive one.
Will executives and employees beyond the security team require training to successfully adopt Zero Trust?
Is Zero Trust just a way for vendors to add fresh spin to old products?
No. Today, Zero Trust is the model that all Federal Agencies must adhere to when designing security architectures for their cloud-based and hybrid computing environments. It’s been defined by reputable, vendor-agnostic cross-industry authorities, including the National Institute of Standards and Technology (NIST), which has published a reference architecture that supplies a roadmap for deploying Zero Trust security within enterprise environments. Zero Trust is now well defined, and it’s possible for any organization to move closer to this ideal.
Are tech companies the only organizations that should consider adopting Zero Trust?
No. In our digital world dominated by data, dependent on cloud computing, connected by mobile devices, and rife with IoT, every company has become a tech company. Realizing and acknowledging this demands a mindset shift. You must view the world through a different lens. This applies to larger global enterprises and smaller businesses alike. You have to accept that technology is at the core of every business. Whether companies host their own hardware or rely on SaaS solutions, nearly every core business function — from HR to accounting and sales — relies on technology. Which is why both organizational assets and sensitive data exist within every corner of IT systems. These resources must not only be secured but also aggressively monitored and actively protected.
Resources


