
Related Post

Report
2024 Identity and Security Trends

Report
Saviynt a Gartner Peer® Insights Customers Choice for IGA

Solution Guide
IGA Buyer's Guide
-1.png)
Solution Guide
PAM Buyers Guide

Whitepaper
Focus on patient care, not complex identity management.
Use our partner finder to discover your perfect business match.

In the days of castle and moat security, defense was simple: the enemy was “out there” and everything “in here” was safe. Now, critical data and assets can live anywhere; every identity and device–-human or non-human, in-network or out—is a potential threat. The US Department of Defense (DoD) is on the front lines of this evolving battleground.
In its recent announcement, the DoD unveiled ambitious goals and timelines for modernizing and aligning its defense strategy with Zero Trust architecture. This initiative would reduce its attack surface, manage risks more effectively, and enable secure data-sharing in coalition warfare. But the first step is investing in the right cloud solution.
In this blog, we’ll explore the pressures driving this paradigm shift, the DoD’s new architecture goals, and the IGA capabilities required to build a modernized cybersecurity arsenal.
As part of its effort to align multi-cloud adoption with its zero trust strategy, the DoD’s Joint Warfighting Cloud Capability contract endeavors to identify cloud-supported software solutions that will move it closer to a fully implemented Zero Trust framework.
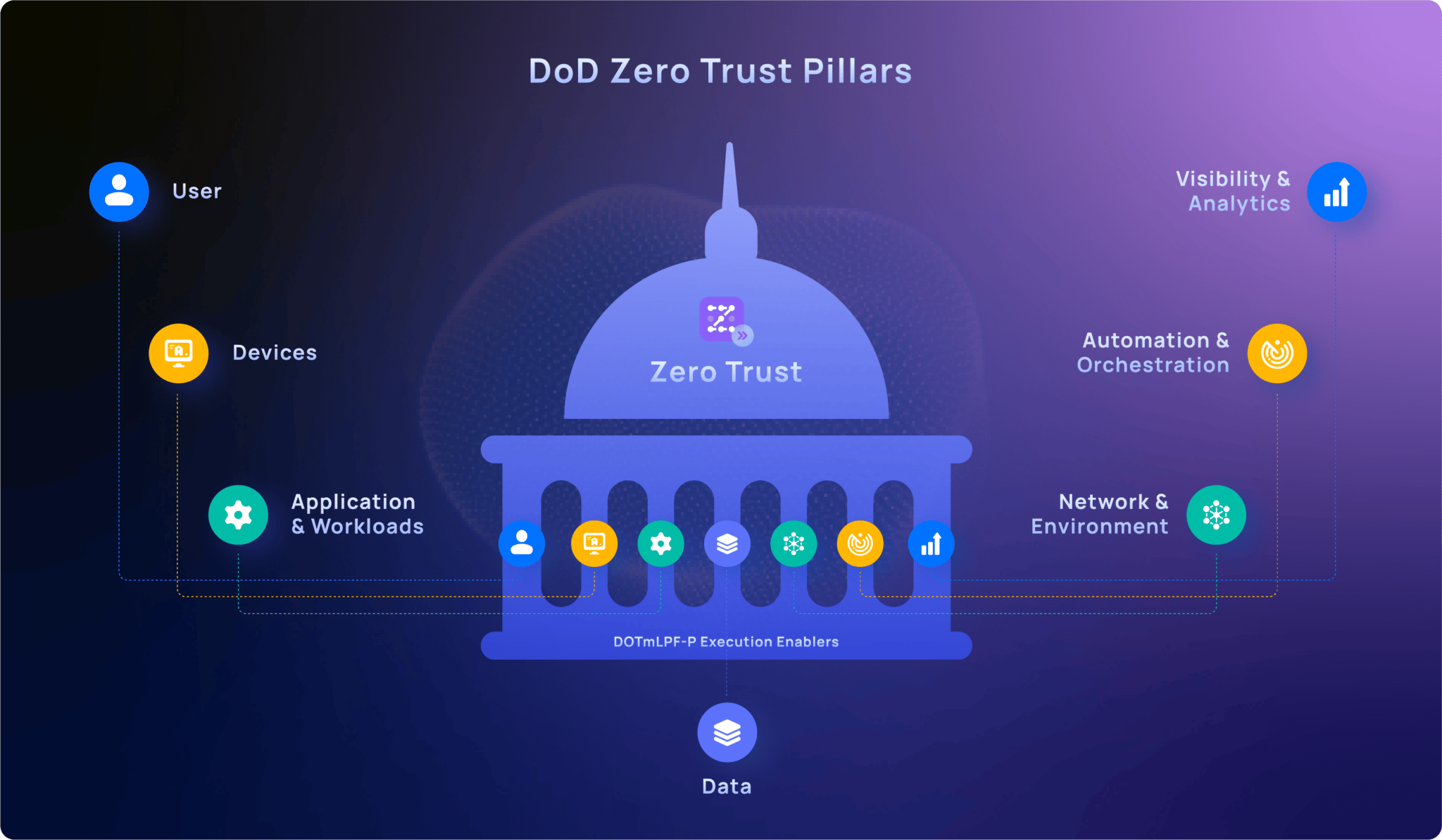
Key features of the Zero Trust Security Initiative that achieve a fully secured DoD IE
At the same time, it must also support warfighters in low-bandwidth, Denied, Disrupted, Interrupted, and Limited (DDIL) mission scenarios, requiring some of the Zero Trust solutions to run on local infrastructure. The timeline is aggressive, with implementation slated for the end of FY 2027.
Beyond bad actors trying to break in, internal weaknesses are legion—74% of organizations say they are at least moderately vulnerable to insider threats, and over half experienced an incident in the last year. Malicious employees, accounts with compromised or orphaned credentials, and systems infected with malware serve as jumping-off points for attacks.
Contractors present another confounding challenge. They are inherently difficult to manage from a security standpoint, with access needs that are temporary and vary widely. At some point, many are re-staffed in a different capacity or move to a different team within the organization.
Security based on administrators and standing privilege worked well for on-prem workforces. Now, “work” happens in a complex and distributed environment, with personnel and resources spread across the globe. Modern workers use software and resources that live in the cloud, migrating between networks of questionable safety. VPN tunnels have capacity issues and require expensive hardware, additional networking, and can present configuration and management challenges.

The expansion in the number of devices, machines, and other NPEs on the DOD Information Networks (DoDIN)–combined with the significant challenge of verifying changes to hardware, firmware, and software–puts undue strain on critical defense teams.
Even in the largest enterprises, on-prem resources are losing their attractiveness. It’s simply cheaper, faster, and easier to use the cloud. The number of SaaS apps increased by 18 percent this year, with enterprises using an average of 130 apps.
But SaaS solutions aren’t always well managed. Over 55% of security executives reported a SaaS security incident in the past two years—ranging from data leaks and breaches to ransomware and malicious apps. With 68% monitoring less than half their SaaS stack, IT departments struggle to know who is using what resources and, importantly, who should be using those resources.
With Zero Trust, every time a user or application submits an access request, all of the attributes associated with that user or application (role, position, duties, usage behaviors, etc.) are evaluated. The security system either auto-grants access or flags the request for further review.
With identity as the perimeter, founded on just in time access, the DoD can move closer to Zero Trust and ensure that:
Before they can protect endpoints with common policies and governance, analysts need a tool that can provide a unified picture of user identities across different cloud solutions. They need telemetry to gauge the maturity of environments and to know where to focus. They need AI to help harmonize data from different environments and track down key data without high-level experts weighing in.

And, if an attack spans different environments, teams need to be able to source the identities involved, verify each user in each environment, and perform entity behavior analysis. With a single source of truth for identities, cyber defenders can operationalize in real-time rather than spending precious time trying to manually connect data and correlate identities across platforms.
The Zero Trust journey is no easy task for even the largest organizations. The most effective approaches to IT security start with investment in the right technology. Here’s how Saviynt can help deliver on core capabilities across cloud, multi-cloud, and hybrid environments:
With Saviynt, any enterprise can achieve a resilient, scalable, and multi-disciplinary cybersecurity architecture that can extend far beyond the “trusted internal zone” of a network.


Report

Report

Solution Guide
-1.png)
Solution Guide

Whitepaper