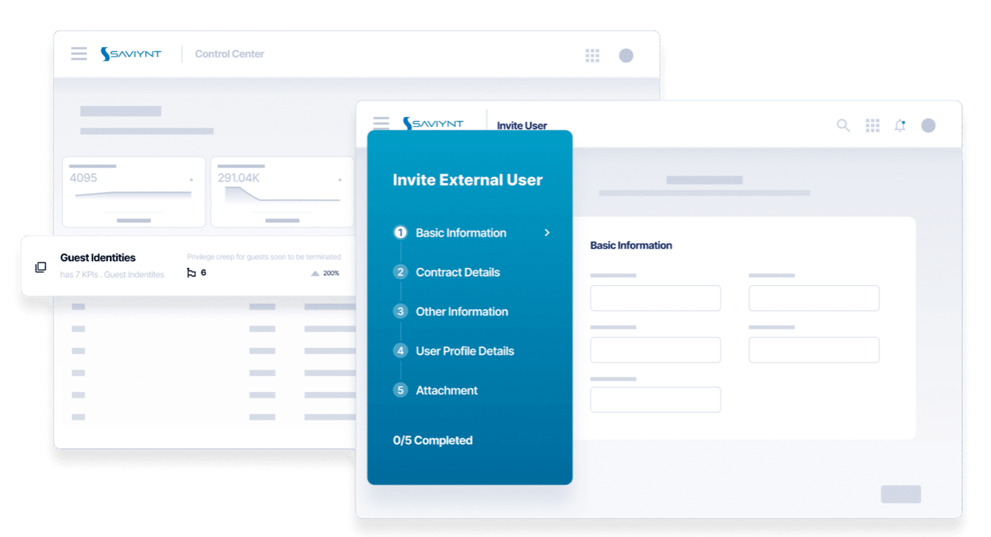
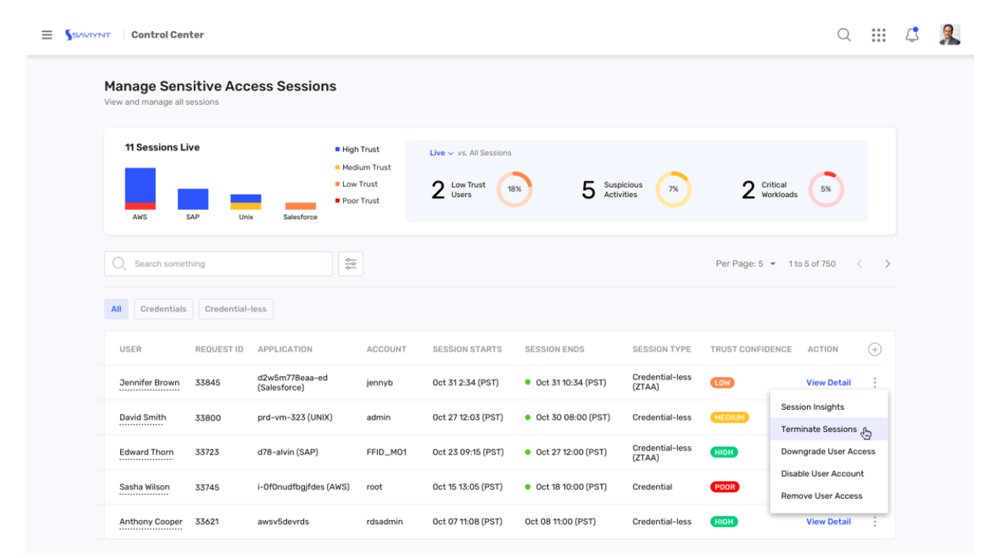
Complexity. Lack of visibility. Large numbers of vendors with no centralized access control. The increasing reliance on third-party vendors in today’s organizations is a cyber attacker’s dream come true.
In March, 2021, more than 1 billion CVS Health search records were accidentally posted online in a data breach incident by an unnamed third party vendor.
In February, 2020, a third-party breach at General Electric resulted in the exposure of personally identifiable information such as names, addresses, Social Security numbers, bank account numbers, passport numbers, and dates of birth. The attacker gained access through a third-party email account.
And the list goes on. One thing’s for sure, it’s imperative to institute an effective third-party access governance program, and that includes managing the additional workload. Here’s an example of how your workload can increase when you add third-party vendors into the equation. Imagine having to manage the identities and access of every employee in your company. Consider all of the different roles and the entitlements that each person should have so that your company can truly embrace a Zero-Trust model of cybersecurity. Now, multiply that by the number of relationships you have with third-party organizations and all of their users and you can see how the workload quickly gets out of hand.
In the first part of this series, we discussed the steps necessary to secure third-party access. The second installment recommends consolidating all of your third-party relationships into a system of record. This allows you to begin to address the biggest challenge with developing a third-party access governance program: most companies have no idea how many third-party relationships they have.
Now, we’d like to focus on the ways you can reduce your third-party access governance workload by using sponsorship and delegated administration to get the work done and stay in compliance.