SAVIYNT PAM CAPABILITIES
Consider Your Critical Assets Protected
Our cloud-based privileged access management (PAM) solution secures privileged access and protects critical assets across your entire infrastructure. Whether on-premises or in the cloud – and for every application – we’ve got you covered.
An Innovative Approach to Privileged Access Management (PAM)
Category-defining architecture with no on-prem footprint
Zero Trust design with just-in-time access and zero-standing privileges
Identity-driven access with integrated risk and governance
Multi-cloud & full-stack infrastructure support
Simple PAM workflows and fast app onboarding
Privileged session management for any app and workload
Bi-directional risk data exchange with third-party security solutions
Visibility into granular privileges across cloud infrastructure entitlement management (CIEM)
WHAT YOU CAN DO
Simplify Management and Monitoring
Manage and monitor the use of privileged access across your organization
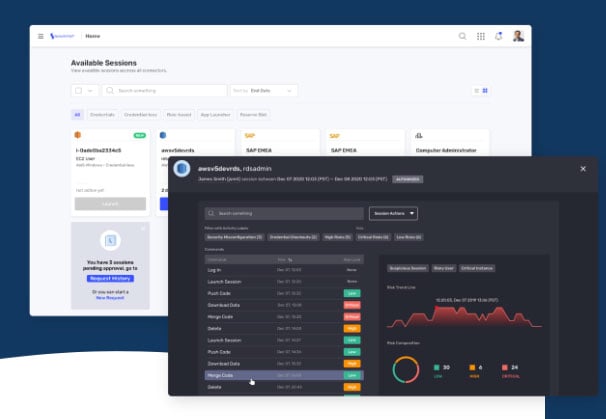
Key Capabilities
- Password Vault - Use multi-purpose vault that stores credentials, keys, and tokens while providing governance – optionally bring your own vault
- Easy Onboarding - Bring in on-prem and SaaS applications via wizard that includes real-time account, workload, and entitlement discovery
- Over-the-Shoulder Monitoring - Monitor privileged sessions with active session termination capabilities
Additional Capabilities
- Password Rotation
- Role-based Access Control (RBAC)
- Command Filtering
- Session Recording with Zero Footprint
- Keystroke Logging
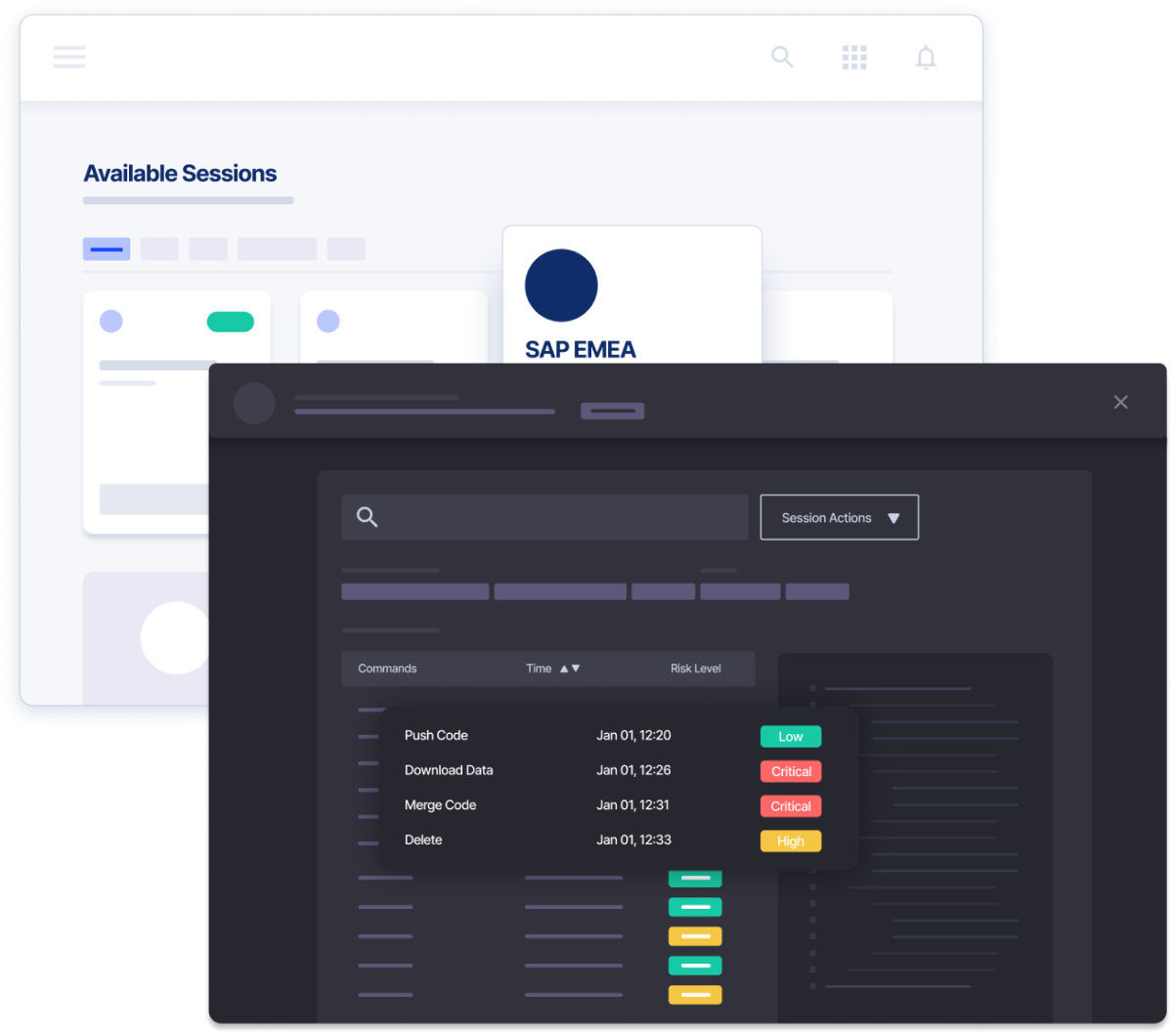
Automate Privileged Account Governance
Use converged PAM+IGA to manage user and service accounts across any platform and application
Key Capabilities
- Identity-Based Access - Streamline privileged access management for any identity or application
- Converged PAM+IGA - Make smarter decisions with governance-driven risk insights and AI-informed privileged access data
- FedRAMP certified - Secure application data with no system vulnerability and continuity of access
- Support for industry-leading cloud service providers
- Support for on-prem resources and web applications
- Service Account Management
- Support for databases (Postgres, MSSQL, & Oracle)
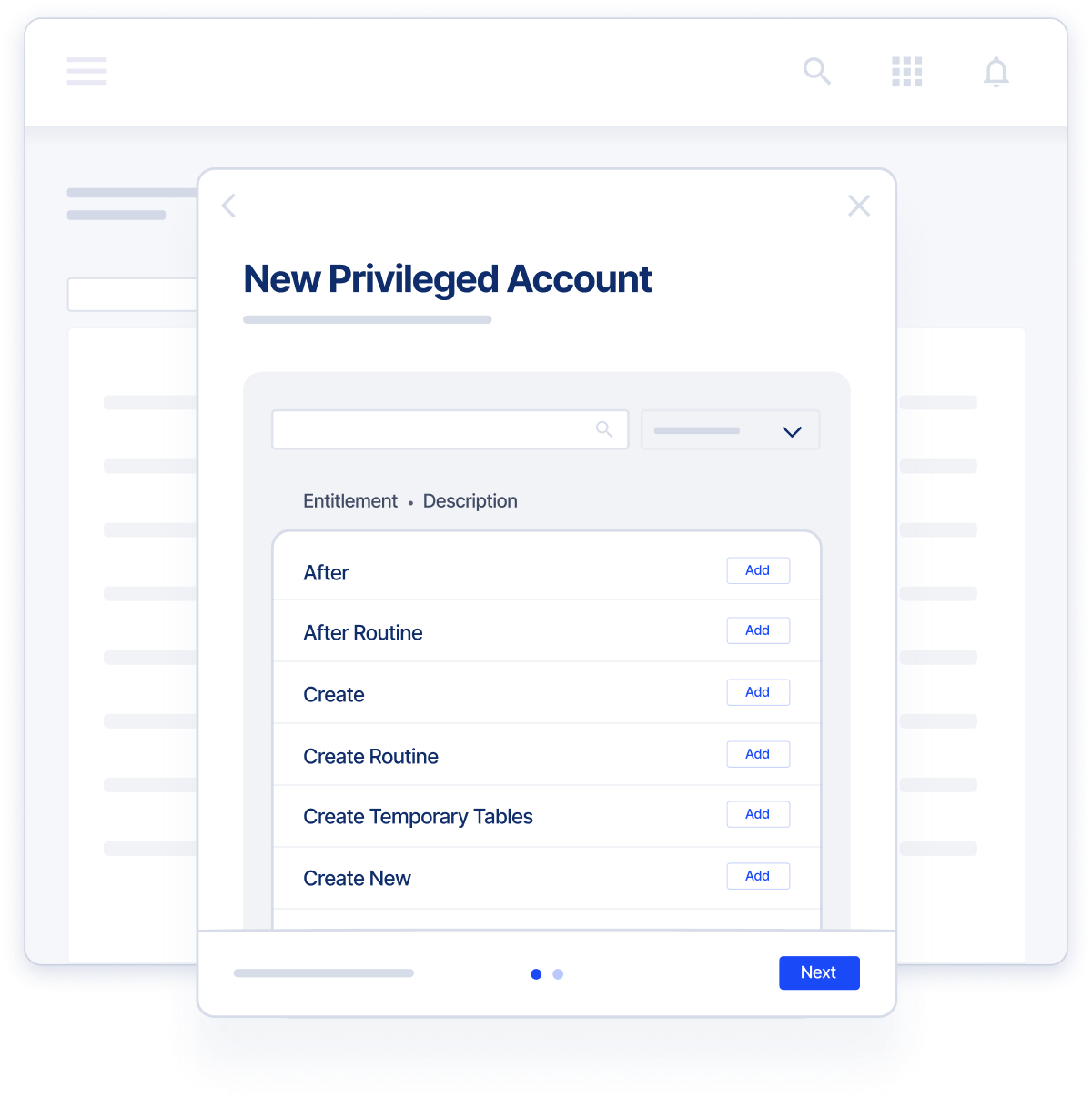
Unparalleled Visibility and Control
Gain security confidence and reduce risk with better visibility and control over users with privileged access.
Key Capabilities
- Risk Visibility & Management - Present risk-aware information and drive better decisions
- Risk-based Access Certifications - Validate system access rights based on risk scoring
- Preventative Controls & Session Termination - Control and terminate risky or unauthorized sessions
- Auditing & Reporting
- Actionable Analytics and Risk Insights
- Non-Repudiation
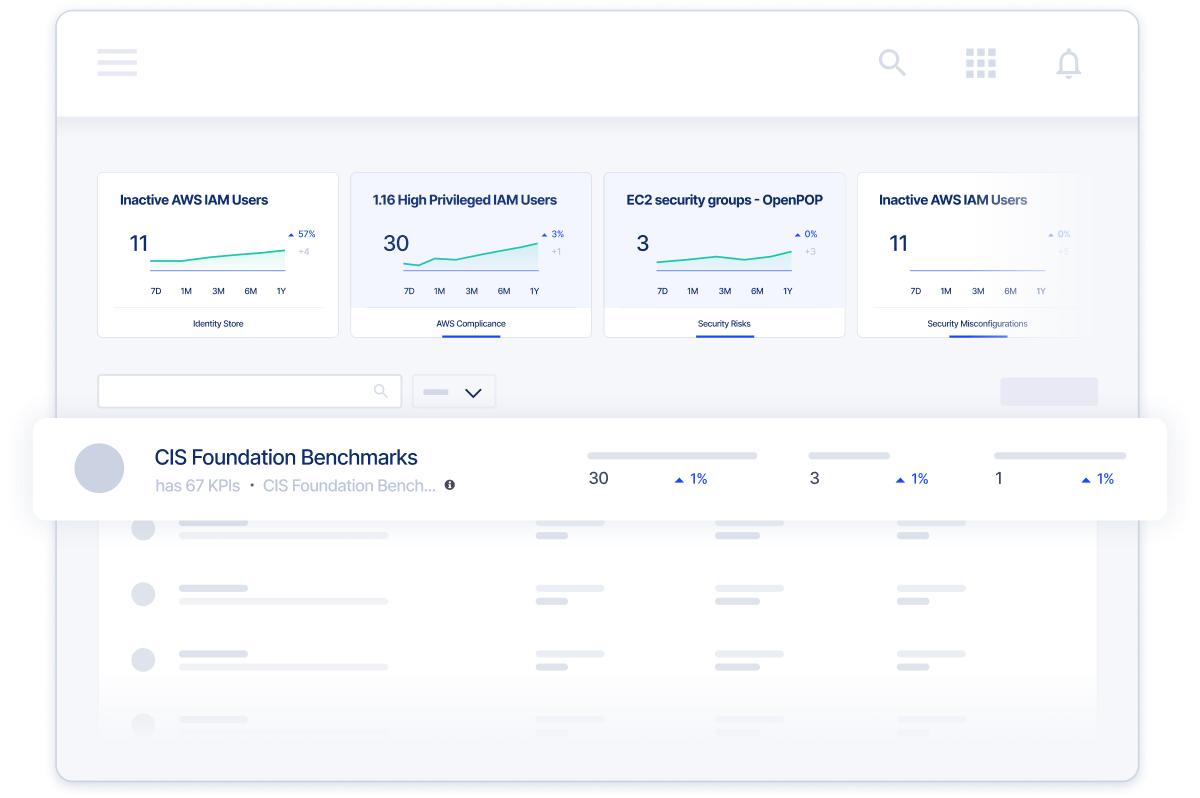
Become a Smooth Operator with PAM
Simplify deployment, lower TCO, and achieve rapid ROI with cloud PAM - no on-prem infrastructure and an efficient user experience.
Key Capabilities
- Open API - Use simple product configurations with a modern user interface
- Drag & Drop Workflows - Quickly build complex workflows with a drag-and-drop experience
- Configurable Data Dashboards - Easily understand pending requests and other activity
- Single Window Admin
- Low- to -no code
Zero in on Zero Trust
Adopt zero-trust principles for any identity and app
.webp)
- Just-in-time Access - Grant users elevated privileges for a limited time
- Zero-Standing Privilege - Automate and scale enforcement of least privilege policies including privilege entitlement clipping and outlier analysis
- Credential-less Access - Hide passwords automatically from users and rotate after use