Zero Trust Security: A Practical Guide for Business
For centuries, moats protected those who lived in castles. They worked well, keeping enemies far enough away that a breach of the castle walls was next to impossible. But then new weapons were developed. So new types of security were needed.
We’re in a similar time of transition today. When everyone worked in company offices on company devices connected to company networks, the old model of using administrators and standing privilege for security (a.k.a. perimeter defense model) worked just fine. But with everything moving to the cloud and remote work becoming the norm in many industries, standing privilege is no longer a relevant defense. People are using cloud software and connecting to cloud data warehouses, roaming from coworking spaces to coffee shops to home offices, working on personal devices, and company-owned ones. Standing privilege doesn’t protect this new way of working, as evidenced by Verizon’s research showing that outsiders cause 70% of data breaches today. The moat still protects, but the castle is much larger, and there are hidden threats inside its walls.
This guide explores a new paradigm that fully addresses all the vulnerabilities created by working remotely on various devices — Zero Trust security. We’ll define what it is and how it works, its benefits, key components, and how to handle monitoring and analytics when implementing Zero Trust.
What is Zero Trust Security?
While traditional security models assume that if you’re on a company device on the company network, you’re authorized to be there, Zero Trust assumes nothing. It requires that those seeking to gain access prove themselves, allowing access for a specific period of time. It also operates on the principle that users should have only the amount of access they need to do a particular job.
Zero Trust evaluates access requests based on micro-segmentation of user types, locations, and other identifying data to determine when to trust a particular user, device, or application. This guarantees that whoever or whatever is trying to gain entrance is authorized.
It works by eliminating standing privilege to lower the impact of compromised credentials and the risk of malware such as CryptoLocker. Using a collection of tools, including identity access management (IAM), Identity Governance and Administration (IGA), and Cloud Privileged Access Management (CloudPAM), Zero Trust better secures remote workforces operating in the cloud.

Benefits of a Zero Trust Strategy
The benefits that a Zero Trust strategy offers go far beyond security. Here’s a look at just how Zero Trust ensures data protection and its five other valuable benefits.
1. Data Protection
The most apparent benefit of Zero Trust is data protection. Once malware breaches your firewall, it can extract your customer data or intellectual property within seconds. Since 86% of breaches are financially motivated, cybercriminals typically seek out this kind of data. A breach can wreak havoc on your reputation and devastate your competitive advantage. However, when your security paradigm always assumes no trust, bad actors have an infinitely more difficult time stealing data. And combining Zero Trust with just-in-time (JIT) access smoothes business processes while preventing rogue employees from gaining access to data they shouldn’t have.
2. Greater Enterprise Visibility
Because Zero Trust never assumes anyone or anything is trusted, it is continuously monitoring activity. It provides visibility into precisely who (or what) is accessing your network. So you know the time, location, and applications involved. And because you can easily monitor all users, devices, and data, at all times, you can more easily enforce compliance. Governance becomes much more straightforward.
3. Reduced IT Complexity
According to a recent survey, 53% of organizations report a problematic shortage of cybersecurity skills. This means a heavier workload for the security team as a whole. Zero Trust reduces the operational complexity of your security program. While it does take additional hardware and services to implement ZeroTrust, the result is less daily work for the operational staff, easing staffing shortages by increasing efficiency. These gains can be expanded by using a solution that centralizes alerts, usage, and access data, so there are fewer interfaces to manage and monitor operations.
4. Less-Demanding Security Workloads
Security teams monitor and manage everything from risk assessments to access requests and security alerts. Security threats are becoming more sophisticated and targeted, resulting in an overwhelmed team. Automation of tedious low-risk access decisions eases the security burden.
5. A Superior User Experience
When you use automation to implement Zero Trust, users don’t have to wait on administrators to approve every access request so they can work more efficiently. With Zero Trust, identity becomes your new perimeter. You eliminate the need for remote workers to log in to VPNs for certain resources. Instead, users go directly to the resources they need and request access or login. Additionally, overprovisioned VPN gateways that slow down access are no longer required.
6. Support for Cloud Migration
Today’s world is in the cloud. Organizations of all types and sizes are moving to cloud-based infrastructure and cloud software solutions. Legacy software tools weren’t built for the cloud. They don’t function well with cloud-based solutions, exposing the network to every user of any single tool. Zero Trust security is ideal for the cloud, ensuring your network is locked down, and users can only access what they need when they need it.
Check out Benefits of Zero Trust to explore these benefits further.
Key Components of Zero Trust
Let’s dive into the components of Zero Trust and explore how they deliver the benefits described above.
Access Visibility Across the IT Ecosystem
Because organizations are using so many data sources and tools, it’s easy to overlook securing a resource, opening your system to an external breach. Another issue is that users often gain wide-open access to the network when they should only be accessing one or two tools, creating unnecessary risk. Using an IGA or CloudPAM solution, the Zero Trust model secures every component and allows you to monitor all activity.
Read Making the Case for Zero Trust Architecture for more on how to secure your network with Zero Trust.
Based on Identity
Identity drives access control in Zero Trust because it’s the only thing that’s reliable. Contextual identity information (such as average peer usage and the requestor’s roles, permissions, and prior access requests) and device information, user behavior, and peer analytics determine if granting access at the specified level is safe. This process is efficient and limits risk.
Limited Access
The purpose of Zero Trust is to limit as much as possible, giving users access only to what they need, when they need it. This approach prevents users from accessing areas of the network that they shouldn’t or accessing tools longer than they should (such as when an employee moves on to another organization). There are four aspects to access limitation:
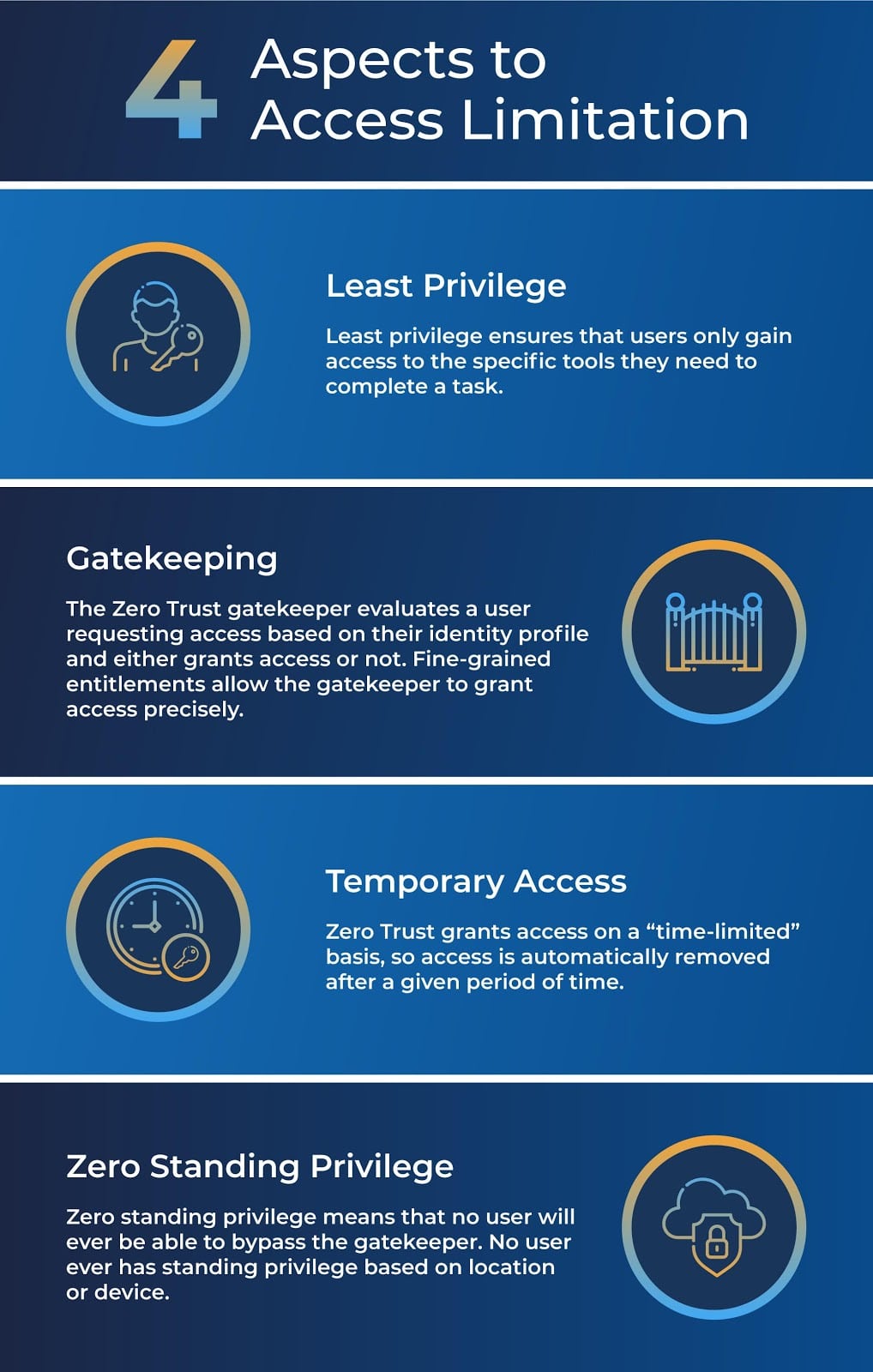
Read How Privileged Access Works with Zero Trust to learn more about limited access.
Assumption of No Trust
With Zero Trust, every time a user requests access, an analysis looks at the user profile and behavior to determine whether or not to grant the request.
Continuous monitoring and analytics are a must for Zero Trust to work. Granting access requires a risk-based analysis. You need user and entity behavior analytics (UEBA) and peer usage data to know what typical user behavior is to spot anomalies. And Zero Trust requires continuous monitoring of all activity related to data access and sharing to ensure relevancy.
Monitoring & Analytics
Let’s dive deeper into the monitoring and analytics that are all-important to Zero Trust. To detect threats, you must have a comprehensive picture of access and usage behaviors for your security platform to analyze and use as a basis for access decision-making. You should be able to identify patterns in access requests that indicate possible bad behavior. (This also helps prevent insider threats, as users who don’t need specific access try to gain access.) Threat detection requires three things:
- Flagging unusual behaviors — You need to know what behavior is typical and atypical, and your security platform should auto-flag potential problems.
- Flagging SoD conflicts — Effective segregation of duties (SoD) controls to reduce the risk of insider threats. As part of Zero Trust, your security platform should flag conflicts.
- Evidence of continuous compliance — You need robust logging of access requests so that auditors can show they meet compliance and for in-depth tracking of what access was granted to which identities.
Zero Trust = Greater Agility
Zero Trust delivers better visibility into how different identities are accessing your organization’s data. This transparency helps you to detect and deal with threats more effectively, both inside and out. And because Zero Trust works seamlessly in the cloud (and with on-prem systems), it’s simpler and more reliable than traditional security paradigms. Additionally, Zero Trust allows you to demonstrate continuous compliance better, decreasing risk. Ultimately, Zero Trust makes you more agile as you can confidently implement new technology without increasing risk.
Watch our Deep Dive into Zero Trust video to learn more about how Zero Trust can empower your security architecture. You’ll learn how to:
- Explore an intelligent identity perimeter
- Achieve Zero Standing Privileges with Just-in-Time Privilege Elevation and time-bound access
- Simplify and streamline dynamic access management with “right-sized” access
- Gain complete control and visibility through continuous risk assessment
- Prevent data breaches and insider threats with real-time insights
- Support multi-cloud and hybrid infrastructure
Saviynt helps ease the move to the Zero Trust Model by drawing the perimeter at identity. Identity centered solutions provide a foundation for Zero Trust. Zero standing privilege, in-depth visibility, automation, and centralized, continuous monitoring are crucial pieces of Zero Trust. Saviynt’s cloud-native solutions offer these components allowing resources to exist anywhere while remaining protected. Talk to an expert about how Saviynt can ease your Zero Trust project by contacting us here.
Related Post




Report
Saviynt Named Gartner Voice of the Customer for IGA

EBook
Welcoming the Age of Intelligent Identity Security

Press Release
AWS Signs Strategic Collaboration Agreement With Saviynt to Advance AI-Driven Identity Security

Solution Guide