Saviynt is introducing a series of capabilities to help customers address the unique security and management needs to manage their external user populations more securely. Two of the landmark capabilities introduced are Identity Verification and External User Classification & Insights.
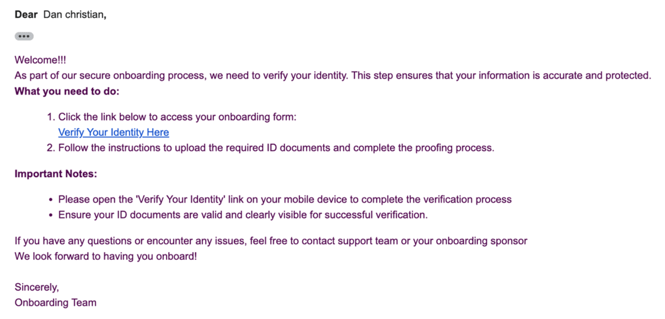
External user populations – identities that are outside of the organization, such as vendors, suppliers, partners, contractors and volunteers may require access to systems and will typically present a higher security risk compared to internal (employee) users. Recent trends also show that in many organizations, the number of external identities are beginning to exceed the number of internal users. In order for our customers to better understand and cater to this risk, Saviynt is introducing User Classification and Insights functionality which offers an easy wizard to start categorizing their external user populations and provide governance insights and recommendations.
On top of that, customers are facing more stringent regulatory requirements, including Sarbanes Oxley (SoX) in the US and NIS2 in the EU which have mandates around reporting third party breaches. Being able to easily classify internal vs. external users without undue burden on IT teams will not only simplify compliance, it can also help organizations build more trust in their supply chains and onboard new users more quickly, providing the right access to the right people.
Regulatory requirements are also evolving in other sectors such as healthcare, finance, and technology. It’s important to make sure that third party relationships can meet compliance needs. This capability will be instrumental in helping organizations with risk assessment and due diligence of their external relationships.
Classify User Identities in Five Minutes
Saviynt customers now have the ability to classify the external user identities, such as vendors, partners, contractors, and volunteers, for better security control. Customers will be able to run a simple, wizard-based report to search for external identities within their existing user population using common parameters, such as email addresses that begin with “c-” or “EXT” or include termination dates.
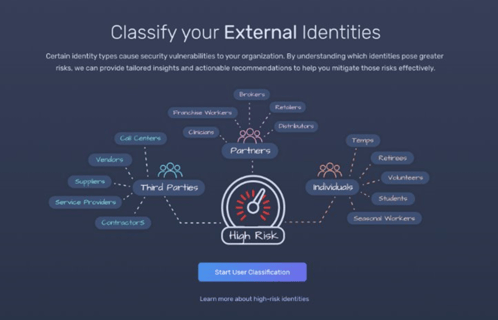
The result of this exercise is a comprehensive dashboard that quantifies their external user base and insights on high-risk conditions like inactive users with active accounts or those with a last logon date longer than 90 days. Customers can focus on mitigating the most pressing risks in the short term and over time will be able to build more trust in their non-employee data to implement more targeted security measures.
Trust Begins With Reliable Onboarding: Streamline Identity Proofing Processes
Another new feature in the February release (Amsterdam) is a new framework to support integration with leading identity-proofing vendors. ID proofing is the process of collecting documentation to confirm an individual’s identity and is often used during onboarding or registration processes for external users. This process is essential for maintaining security, preventing fraud, and ensuring compliance with organizational or regulatory requirements.
Saviynt customers can seamlessly connect their identity-proofing solution into The Identity Cloud within a few clicks. From there, internal sponsors can invite and onboard their external users with the Create User Request Form.
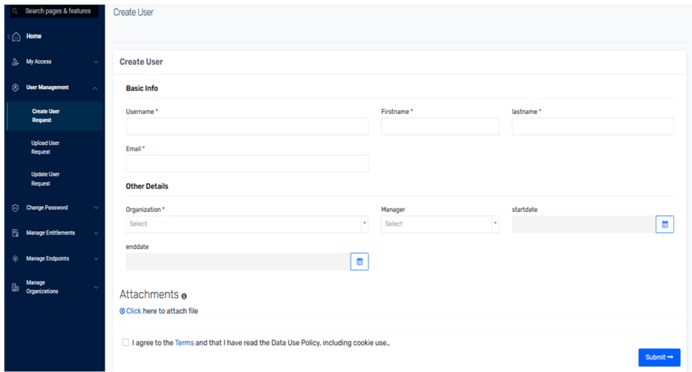
This triggers an identity proofing event and an email is sent to the external user for verification. The user receives a text message to capture images of their government-issued ID or a one-time notification to confirm their identity and complete the verification steps. All of this has been designed to create a seamless, intuitive experience for internal sponsors and external users alike, while reducing the burden on IAM teams.