Cerner Shares Best Practices for Transitioning to a Cloud Identity Platform
Founded in 1979 as a health information technology company, Cerner works at the intersection of health care and information technology to connect people and systems worldwide. Comprising over 30,000 employees and contractors in 26 countries, this healthcare technology titan uses the latest innovations to create solutions that help communities and people take charge of their health. So, it stands to reason that Cerner took a proactive approach to the health of its identity governance administration.
Attendees at CONVERGE 20 attended an in-depth breakout session where David Kendrick, Manager and Technical Solution Owner of Identity Access & Governance for Cerner, discussed its ongoing efforts to modernize Cerner’s IGA-related processes and technologies. Although Cerner is still early in its modern identity journey, David was able to share key insights learned while laying a new foundation for the future success of the program.
In his talk, David addressed several key areas enterprises should consider when transitioning to a cloud identity platform like Saviynt, including how to:
- Establish Governance processes
- Improve provisioning workflows and reduce or eliminate known problems
- Manage the provisioning process for cloud infrastructure (AWS & Azure)
- Implement Zero Trust Architecture to Support HITRUST
If you missed the session, you can watch it on demand below to get a better understanding of Cerner’s ongoing IGA implementation – and David’s best practices for organizations as they look to modernize identity & access governance. Filled with top tips and careful considerations, David covers how to take a programmatic approach to deployment and accelerate user adoption. For your convenience, the transcript is included below the video.
Watch the Breakout Session
Read the Transcript
Jason Gzym:
Hello, and welcome to the Laying a Solid Foundation for Modern IGA breakout session. My name is Jason Gzym. I’m a director of Solutions Engineering and Strategy at Saviynt. I will be hosting your session today as we discuss going from concept to implementation at Cerner.
Prior to joining Saviynt five years ago, I spent two decades as a practitioner within Identity, Governance, and Security spaces with a focus on the healthcare vertical. Helping the healthcare community realize the benefits of identity and cybersecurity to improve patient care has been rewarding. And it’s brought me great satisfaction.
I am very excited today to listen to our speaker. But before we get started, I’d like to share some quick housekeeping tips to know for this session. First, know that this session is live and will be recorded for all attendees to access on-demand after the conference ends. Second, we are holding a live Q&A session during today’s session. We encourage you to submit your questions using the SpotMe platform via the chat feature. Our chat moderators are standing by and will provide me with your questions. With that, I would like to introduce today’s guest expert, David Kendrick.
David Kendrick is a manager and technical solution owner for Identity and Access Governance at Cerner. David has over 20 years of IT experience that ranges from the area of CRM, IT service management, collaboration, finance in Identity, and Access Governance. He’s currently a manager and Technical Solution owner for the Identity and Access Governance team within services at Cerner.
His responsibilities include providing guidance to a geographically diverse team of software and system engineers and project managers. Additionally, he maintains roadmaps for several related applications, ranging from On-premise, COT systems, SaaS, and Custom develop web applications. All solutions provide capabilities regarding identity management, multi-factor authentication, credential management, and user authentication. With that, please welcome to the stage David Kendrick. Thank you, David.
David Kendrick:
Thank you, Jason, for the introduction. Good morning or afternoon. I appreciate the opportunity to speak at CONVERGE. This is my first year attending. So as Jason mentioned, I am the manager of our Identity Access and Governance team. Within Cerner, my focus is more on our technology, and we partner closely with our Enterprise Security Organization as well. Throughout the presentation, I want to begin by discussing our company’s efforts to modernize our IGA related processes and technology.
We’re still in the early stages of our implementation. So we’ve not hit that finish line yet. So quite the journey to continue, but we kind of talk through the steps we are taking, the reasoning behind why we started this process in the first place, and hopefully provide some insight on how you can improve if you’re starting a similar journey.
So I want to start with some background about Cerner, just to provide some context with some of the challenges that we’re presented with and what we’re trying to solve. So, to give it a high-level overview of Cerner, Cerner is a health information technology company. Having been around for a little over 40 years, we have over 30,000 employees and contractors globally. As you can see on the map, we have offices; they are across over 26 countries. We have clients that we work with in over 35 countries. We’re headquartered in Kansas City, Missouri, and then we have global data centers in seven countries.
We have to take into consideration the multiple access related policies and have in many of those that present some identity-related concerns that we need to be made aware of. So why did we choose Saviynt? So we have a legacy solution. We’re not new in the Identity Access and Governance space. We’ve had space for nearly the last 10 years. So we have quite a bit of experience on an existing platform. However, that platform hasn’t necessarily been able to grow over time as much as we’ve needed to as a business.
“We wanted a more modern approach, a more cloud-first approach.”
So the current solution right now takes a fair amount of effort to implement new integrations into applications that we’re onboarding now. As you can imagine, the types of solutions where we are working with now, versus 10 years prior, have changed significantly as most of the industry has changed — whether it’s going to a more SaaS model. Absolutely, so we are trying complicated workflows that we’ve been struggling to keep working properly and keeping up with the volume.
So we wanted to end up back to figure out what it is, how do we move forward into the future? So we wanted a more modern approach, a more cloud-first approach. Our current solution is On-premise, which means we have significant infrastructure costs that we have in place. I think I actually heard it mentioned earlier today during the keynote speaking engagement about reducing the company’s capital expense in that area. And that’s certainly one area we’re focused on why we wanted them to go down software as a service approach. Also, there’s significant expense in managing an on-premise solution, whether we’ve done multiple upgrades, which take a lengthy amount of time. We have to have a very large team, a large stack of servers to be able to support. We want to try to optimize where we can in that regard.
“There’s significant expense in managing an on-premise solution, whether we’ve done multiple upgrades, which take a lengthy amount of time. We have to have a very large team, a large stack of servers to be able to support. We want to try to optimize where we can in that regard.”
So quickly going over… It looks like we’re having a little bit of an audio problem. So let me switch. Okay. So, to talk about goals, what we wanted to achieve as we’re going through this process. We wanted to first and foremost establish governance processes. So, we do have governance processes in place today. But we do not have an excellent governance solution to support those processes. That’s one of the things we are looking to achieve here with Saviynt. I have a slide later on about that.
We’re also looking to improve our provisioning workflows, cutting back on any known errors that we have with those processes. A key point to us starting this project was really envisioning what we wanted those provisioning workflows to be. We, as most companies, are moving into Cloud Infrastructure. We actually have both AWS and Azure environments. So we wanted something that had native capabilities in both of those spaces. And then the last year semi-related, we’re wanting to work on implementing a Zero Trust environment. And then we’re also looking to achieve HITRUST certification.
“We do have governance processes in place today. But we do not have an excellent governance solution to support those processes. That’s one of the things we are looking to achieve here with Saviynt.”
Overall high-level timeline. We’re breaking our first implementation into multiple phases with the goal of being completed in the middle of next year. We’ve started in the middle of this year. Honestly, this year’s planning was a bit different as most projects are typically planned without the use of whiteboards and being able to co-locate and work out plans.
So we’re breaking it down into these different components. Obviously, getting our environment configured, reviewing our HR workflows, and then setting up our integration. Our system of record for HR data is Workday. So we are leveraging Saviynt’s Connector with Workday. That was a key feature for us to be able not to start an integration from scratch and be able to leverage an existing integration there for the solution that we already had.
And then, we are working on implementing our integration with AWS as our first Cloud Infrastructure Connection. So we’re trying to wrap that up. We’re in the middle of completing those Workday and AWS integrations at the moment, and it looks like we will get our initial integration standing up by the end of the year. We’ll have a few more smaller iterative releases into Q1 to tweak some of that. And then, with the goal in mind there, is to be able to achieve our HITRUST requirements that we have with our AWS environments.
We need to be able to support Enterprise Security, and our company’s needs to provide that certification. Then at the end of next year, we’re looking to really focus on redesigning those existing provisioning workflows that we have. And then, from a governance perspective, really build out those access certifications as well.
So the next thing I wanted to get into is the details behind our goals that I just covered, including what are best practices for implementing any Identity Access and Governance related solution, or in many of these cases, some of the processes going to be applied to other projects as well, regardless of their particular focus, but within the Identity Access space Governance as I mentioned, is a big item for us to tackle while we have processes in place. Many of them are manual and take a fair amount of focus and effort amongst the teams that are working to support those governance processes.
As a healthcare-related company, Cerner is obviously subject to a number of regulatory bodies. So, we do have to frequently undergo audits related to our access policies, at a minimum, on a quarterly basis. But frequently, we’re actually being audited in many cases by multiple governing bodies, which require us to go through this process fairly frequently and given the manual nature of the processes we have in place. It is imperative that we’re able to get to the data as quickly as possible and make sure we’re providing accurate information.
So, as we’re going through here to establish our governance processes, we want to develop the access reviews and certification campaigns. So we’re really wanting to start leveraging that native capability that exists within Saviynt security manager, where our current tool does not provide that capability. And then also leveraging that native audit reporting capability that exists there.
We feel that this will provide us with a significant improvement in efficiency in our processes. So that way, we’re able to not only require less technical people to be able to support those audits, we’ll be able to push out that in a more timely manner without having to take sometimes days to provide the information that the auditors have requested.
So when it comes to Account Provisioning, this is the bread and butter of our onboarding and offboarding processes. We wanted to not just re-implement the processes that we had in place. So one of the key items or desires for us was to start from scratch with our processes so that we can figure out where we need to improve.
So with the goal of the processes reviewing that, we ended up truly starting from scratch. Documenting what we do today for the various onboarding and offboarding but then as we went through there, we were definitely focused on identifying areas that we knew we had bottlenecks with the process, or if we had things that were just flat wrong with the way business is currently managed.
Business has changed since many of those processes were initially implemented over the last several years. So we really looked to identify and call those out, get agreement across our HR and Enterprise Security Organizations to agree with the desired outcome. So that’s what we ended up walking away with. And we have completed that activity and are coming away with new workflows that we can then, in turn, work on implementing as we’re standing, Saviynt up over the course of the first half of next year.
With the goals of our provisioning processes. We want to be able to automate as much as possible and reduce any complexity there. The more complexity, as everybody’s well aware of, the more things that can go wrong. So we want to simplify if, at all possible, we also had the same mindset of simplifying it from the end user’s perspective too. We want to make sure that they have it as easy as possible, an opportunity to request access and go through the process of knowing what they need to request, knowing who needs to provide the approval. And so we were keeping that in mind, too, to keep that user-focused.
And then the last key component in here regarding provisioning and access that we’re really excited to leverage is, we did not have the capability today to do role mining and take advantage of the machine learning capabilities that Saviynt provides. So, we are very interested in leveraging that role mining capability and access policies. So that we can take advantage of the automation, making sure that people are getting the access that they need and as painless as possible methods.
So as I mentioned, we do have both AWS and Azure environments. From an AWS perspective, Cerner is looking to implement many of our healthcare solutions in the AWS space, where Cerner partnered with AWS publicly last year. And so, that’s a big focus for Cerner to be able to modernize those systems and be able to move into the cloud and take advantage of AWS’s offerings there. Likewise, we have a number of corporate law-related applications that we’re looking to host and do host in Microsoft’s Azure Infrastructure.
So we have a need to be able to integrate and manage access to both of those cloud providers. That’s another area that, with the current solution, we did not have the native capability to do. The current solution was created before those cloud providers even existed. So it didn’t have that natively.
So we are leveraging that capability right away with the AWS pieces. But we plan on integrating with Azure as well into next year. We really want to manage our risk and access across those different cloud environments to make sure that we know who has access, what privileges they have with that, being able to perform that the proper access certifications in those areas, and with the ultimate goal of being able to provide a faster transformation of our DevOps and SecOps processes, where we do have limited capability today. So we definitely see this as a big win for us implementing Saviynt.
“With the Zero Trust Architecture that we’re headed towards. We want to make sure we’re implementing more control of who can access our systems and making sure that we know what steps they need to follow to gain that access.”
With the Zero Trust Architecture that we’re headed towards. We want to make sure we’re implementing more control of who can access our systems and making sure that we know what steps they need to follow to gain that access. We want to limit Birthright access. Currently today, we’ve probably over-provisioned unnecessarily, mainly because we don’t have the more fine-grained controls that are necessary.
So we’re wanting to head towards more of the least privileged access approach that I’m sure many of you are familiar with. And going down to this Zero Trust Architecture, we’re wanting to improve those request processes to reduce complexity so that people do know what they’re requesting access for and making it as easy as possible.
We are really planning on leveraging risk-based access policies as well. It all comes down to being able to control, being able to audit, and knowing who has access, only providing access over the period of time in which they need it. We do have a number of capabilities that limit the time period in which people have elevated privileges.
So we want to make requests for those elevated privileges, go as smoothly as possible so that people don’t find it cumbersome. Don’t look for ways around the process. Just make it as smooth as possible but still providing that visibility that we need. And then the last here, identifying HITRUST access policies and controls to ensure we’re supporting that. We are in the earlier stages of working through all of those HITRUST related details as well.
So some of our lessons learned through this process (some I mentioned) we’re not even quite halfway through the project. But we’ve led many large projects with Cerner as well for varying topics. These lessons tend to be true no matter what the topic happens to be or what the area that you’re trying to implement.
My last point here is actually one I’ll touch on first where it says plan, plan. Honestly, I come from a project management background too. And when it comes to implementing any new solution, planning is key. You can’t expect to complete the project without knowing what your goals are in mind and knowing how to split the project up into manageable pieces.
So that’s why I believe strongly in the process that we started with the HR processes, making sure that we started from scratch, identifying the bottlenecks and areas for efficiency and improvements. It’s definitely going to be key for us. I don’t believe in implementing one solution following another and just implementing the exact same capabilities. Then we won’t end up growing. If we go down that path, we don’t improve any processes. And all we’re doing is switching one solution for another with little to no change to the business.
So we are heavily planning here. We have been thorough in evaluating what the solution needs to make sure that we are moving the needle, so to speak, for our business. This is key. Nobody gets excited about implementing an Identity and Access Governance related solution within our corporation.
We operate behind the scenes and undercover. So we want to be as efficient and functional to manage the business needs. Our business has changed significantly, even over the last few years. And we anticipate that business will continue to change quickly. And we need to be able to pivot as the business needs change. So with that, I’ll wrap up by thanking everybody for listening to my presentation. And then I know we have an opportunity to… If through my session, if you had any questions for me to attempt to answer those questions as well.
Jason Gzym:
Thank you, David. I appreciate that. So yeah, I think we’re going to open up the session for an audience with Q and A with David. If you haven’t already, in the live stream, please submit your questions using that chat feature via the live session. And our chat moderators, they are standing by to share your questions with David and myself.
{End of Transcript}
Want more CONVERGE 20 insights? Watch all customer sessions on demand here.
Related Post


12 / 19 / 2025
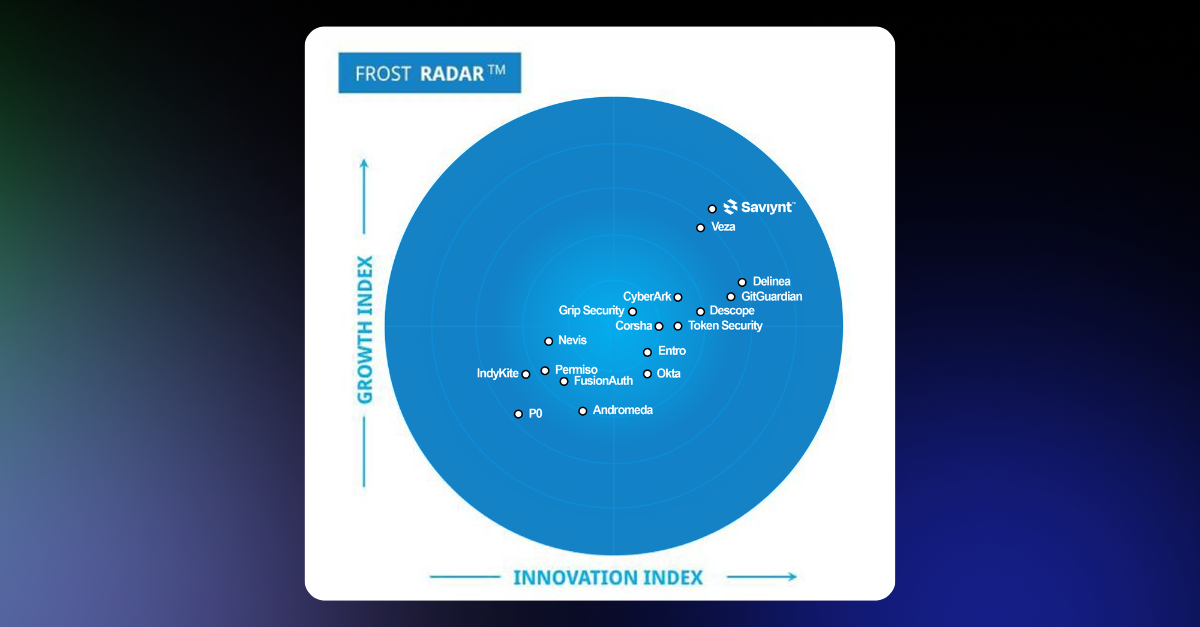
Saviynt Recognized as a Leader in Frost Radar™: Non-Human Identity Solutions, 2025
READ BLOG
Report
Saviynt Named Gartner Voice of the Customer for IGA

EBook
Welcoming the Age of Intelligent Identity Security

Press Release
AWS Signs Strategic Collaboration Agreement With Saviynt to Advance AI-Driven Identity Security

Solution Guide