What is Identity Access Management (IAM)?
What is IAM?
Identity and Access Management (IAM) solutions ensure that the right users have the right access to the right IT resources, at the right time, for the right reason, so they can do their job.
IAM software — combined with Identity Governance and Administration (IGA) solutions — extends and defines the who, what, where, when, how, and why of technology access. By basing your enterprise IT strategy on your identity access management program, you create a foundation for managing new technologies’ data privacy and security risks.
These identity and access management programs are designed to protect data security and privacy. This process starts with user authentication and authorization — often using a single sign-on solution that incorporates multi-factor authentication — and then assigns access rights to resources with identity management (IDM) solutions to continuously monitor access. IAM solutions provide enforcement of and governance over “least privilege” access rights.
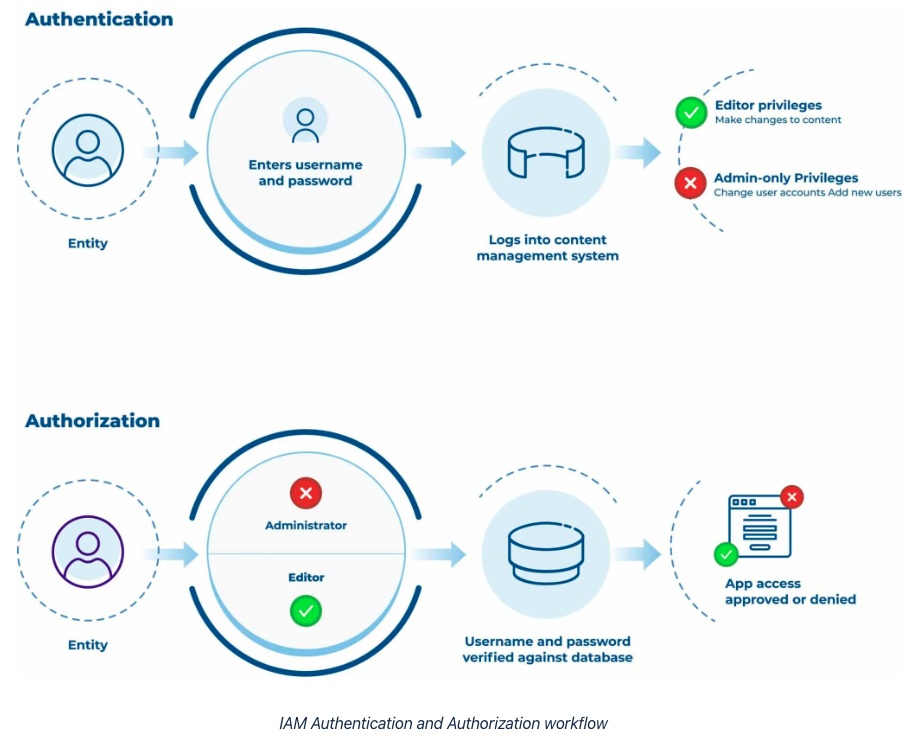
Identity and access are two parts to govern how your users interact with data and applications across your information systems, networks, databases, and software. Let’s further break down the identity and access management definition and terminology.
What is identity when it comes to IAM?
Historically, before digitization and business transformation initiatives, identity consisted solely of human users, such as employees or on-premises contractors. Today, an identity can be any human or machine (IoT device, cloud workloads, code, bot, etc.) that interacts with your IT systems.
For example, an on-premises employee is one type of identity that presents a particular set of risks. In contrast, a remote employee is an identity that brings a different set of risks. Meanwhile, robotic process automation, code that manages administrative tasks, through the use of service accounts, is another kind of identity from an Internet of Things (IoT) device.
What is access in the context of IAM?
After creating an identity for an individual or a non-human identity, you must determine what resources that identity can access. For example, whether human or not, each identity needs access to the resources that allow them to do their jobs. Access cannot exist without identity. However, identity is useless without providing access to resources.
Identity and Access Management (IAM) in the Workplace
As your organization increases the number of resources, you also increase the number of applications to which you must authorize your users. For example, suppose you use a shared drive for collaboration and a sales enablement tool like HighSpot. In that case, your sales team members need access to at least two different services. As you add more Software-as-a-Service (SaaS) applications, you increase the number of tools that require authentication.
Most organizations manage their identity data with an active directory, a large data repository that contains all ID information. After building the directory, they connect it to their applications and environments. If you follow identity and access management best practices, you also want to incorporate multi-factor authentication (MFA). MFA requires your users to use more than one of the following authentication methods: something you know (password), something you own (smartphone, token), or something you are (biometrics).
Once identities are established, access management can get complicated. For example, within higher education institutions, a university professor can hold multiple identities that require access to different resources. As instructors, professors need access to sensitive university information such as students’ grades and advisors. Meanwhile, many universities also allow faculty and staff to take classes for free. As students, professors should only have access to their information, not their classmates.
Identity and Access Management’s Business Impact
The proliferation of accounts wreaks havoc on IT administrators. Each account needs an identity and a way to authenticate its own set of rights within the ecosystem. The IAM risks inherent in modern IT infrastructures lead to security, privacy, operational, and compliance risks.
Information Security Risks
IAM risks increase as organizations create complex IT infrastructures. According to the 2021 Data Breach Investigations Report, 34% of data breaches involved internal actors. Additionally, 15% of data breaches involved authorized user privilege misuse. The report detailed that privilege misuse was one of the top three data breach patterns for the Financial and Insurance, Healthcare, Public Administration, Manufacturing, and Retail industries.
Another infosec risk to consider relates to personal privacy–specifically, giving people control over their personally identifiable information (PII). For example, Human Resources may need access to an employee’s medical history. However, that employee has the right to keep the information private from a manager. If your company is not following identity and access management best practices, you may be violating someone’s right to privacy.
Operational Risk
IAM technology also protects you from operational risks such as embezzlement and fraud. Organizations can use IAM tools to manage Separation of Duties (SOD). For example, a person accessing Accounts Receivable should not access Accounts Payable. If the person can access both, they can create a fake vendor account and pay it from the corporate bank account without oversight.
Compliance Risk
Depending on your industry, you likely need to meet regulatory compliance requirements. Most regulations require organizations to limit access to data. For example, under the Health Insurance Portability and Accountability Act (HIPAA), a healthcare provider can face fines ranging from $100 to $50,000 per violation.
A robust IAM and IGA program can provide proactive threat visibility and risk mitigation while helping meet more specific compliance criteria laid down by various regulations, including the following commonly encountered recent laws.
Saviynt & Assured IGA Compliance-as-a-Service
Saviynt’s IGA platform offers a Control Exchange with over 200 regulatory, industry standard, and service provider controls available out of the box. We offer connectors with the most-used cloud services providers and applications. This frictionless onboarding enables you to create an authoritative, standardized source of identity with fine-grained entitlements across the entire IT ecosystem.
With Saviynt’s Control Exchange, you have over 200 built-in controls to track access and usage, create key performance indicators, and streamline compliance documentation.
Visibility into Who, What, Why, and How
Saviynt enables organizations to merge divergent identity, role, and group definitions across their on-premise, hybrid, and cloud infrastructures to create a single, authoritative identity source. The platform natively integrates with business-critical IaaS and SaaS products, and organizations can limit access beyond the coarse-grained application level and drill down to the “edit/read” level using fine-grained access entitlements.
Saviynt’s analytics streamline the request/review/certify process by aligning with policy controls. The platform alerts users to anomalous requests/access which an administrator must approve. Our peer- and usage-based analytics enable organizations to maintain “least privilege” controls and prevent SOD violations.
Questions People Often Ask About Identity and Access Management (IAM)
What are the IAM Compliance Requirements for the Health Insurance Portability and Accountability Act (HIPAA)?
An IAM solution that addresses HIPAA standards must include:
- Credential protection through the use of single sign-on
- Federated identity management for simplified integration of healthcare business partners
- Centralized access governance to curate HIPAA-compliant access management across organizational infrastructure
- Automatic access logging ensures compliance with HIPAA security rules such as tracking access to patient data
- Automated reporting stems from the logging and is used to facilitate auditing of HIPAA security compliance.
Healthcare-related businesses benefit from the implementation of IAM solutions that includes federation, single sign-on security, centrally managed permissions, and automated logging. Administrative transactions become less complicated with effectively managed rights and proper account termination. Also, automated in-depth logging enables HIPAA auditors to verify electronic media policy compliance.
What are the IAM Compliance Requirements for the Gramm-Leach-Bliley Act (GLBA)?
An IAM solution can proactively address provisions in The Safeguards Rule and improve GLBA compliance through:
- Role-based management to ensure access through user roles rather than direct user assignment
- Controls to ensure segmentation of duties to prevent risky access situations
- Automated provisioning and de-provisioning of users as personnel change roles and jobs
- Entitlement management to limit permissions to only access what is needed for a user to complete their job.
- Multi-factor authentication to protect data in the event of user passwords being compromised.
Organizations found not to be in compliance with GLBA face significant financial penalties. GLBA security violations extend to individuals who not only risk financial penalties but also potential jail time for those who ignore or willfully circumvent security safeguards. Enforcement of GLBA is handled by the Federal Trade Commission (FTC).
What are the IAM Compliance Requirements for the Family Educational Rights and Privacy Act (FERPA)?
FERPA compliance requirements an IAM solution should address include:
- Federated infrastructure allowing eligible non-university affiliates access to relevant education records.
- Means by which students can delegate access to 3rd parties to access their education data.
- Accurate and complete logging of users with access to student data including timestamps.
- Automated reporting providing audit-worthy access management evidence.
FERPA compliance includes the right of a student to restrict access to their directory information in spite of it being public information. FERPA regulations also allow eligible students to grant or revoke permission for their parents to access education records. The ability to easily manage and track access management is the key to privacy law compliance. IAM solutions that centrally manage and cross-reference accounts of eligible students and their parents, as well as school staff and faculty, must ensure that controls are in place limiting access to student records as appropriate.
What are the IAM Compliance Requirements for the Sarbanes-Oxley Act (SOX)?
SOX security standards call for internal controls that are tested and documented to be in place for preparing financial reports and for protecting the data integrity of the accounting information going into these reports. IAM solutions that address SOX compliance requirements include:
- Centralization administration of access management and identity governance.
- Enforcement of segregation of duties (SoD) policies.
- Regular auditing to verify user rights and permissions across the infrastructure
- Automatic logging and tracking tools that generate clear reports for compliance audits
SOX addresses both physical and digital records making IAM an integral part of compliance, but the key to aligning with SOX requirements is the ability to produce on-demand evidence for an audit. By automating IAM activities including user provisioning and de-provisioning, granular conditional access controls, and implementing accurate access logging and usage tracking companies improve their security posture and reduce the risk of data breaches.
What are the IAM Compliance Requirements for the California Consumer Privacy Act (CCPA)?
IAM solutions that assist in the satisfaction of CCPA compliance requirements for privacy and data security must include:
- Identity management capabilities that tie individual consumers to their data and privacy requests
- Access Governance to ensure that a company knows where the data is housed and who can access it
- Strong authentication including multi-factor authentication to protect disclosure to unauthorized users
- Centralization administration of access management and identity governance.
As a key factor of CCPA, consumers are in control of their privacy and personal information with rights to deny or revoke either the collection or sale of their data. While this parallels in data protection with GDPR, it differs in enforcement. With GDPR, violations can cost up to 20 million euros or 4% of global revenue, whichever is greater, while CCPA implements fines on a per violation basis that cap at $250,000 per violation.
- What are the IAM Compliance Requirements for the New York SHIELD Act?
IAM solutions that address NY SHIELD Act data security standard should include:
- Automated provisioning and de-provisioning of users as personnel change roles and jobs
- Entitlement management to limit permissions to least privileges
- Federated identity management to simplify integration and tracking of business partners
- Multi-factor authentication to increase the difficulty of stealing credentials to illicitly access data.
SHIELD compliance necessitates that an organization minimize the risk of a cybersecurity breach or deal with the financial impact of costly breach notifications. Implementing a robust IAM solution not only proactively protects, but it improves the overall security posture of organizations, ensuring compliance and minimizing risk.
What’s the difference between IAM and IGA?
IAM and Identity Governance Administration (IGA) may sound similar but there are notable differences. Gartner notes “IGA differs from IAM in that it allows organizations to not only define and enforce IAM policy, but also connect IAM functions to meet audit and compliance requirements.” To elaborate, IAM is focused on provisioning and deprovisioning while IGA allows for the governance and administration of IAM policies and relevant reporting for compliance purposes.
What are the IAM Compliance Requirements for the Family Educational Rights and Privacy Act (FERPA)?
FERPA compliance requirements an IAM solution should address include:
- Federated infrastructure allowing eligible non-university affiliates access to relevant education records.
- Means by which students can delegate access to 3rd parties to access their education data.
- Accurate and complete logging of users with access to student data including timestamps.
- Automated reporting providing audit-worthy access management evidence.
FERPA compliance includes the right of a student to restrict access to their directory information in spite of it being public information. FERPA regulations also allow eligible students to grant or revoke permission for their parents to access education records. The ability to easily manage and track access management is the key to privacy law compliance. IAM solutions that centrally manage and cross-reference accounts of eligible students and their parents, as well as school staff and faculty, must ensure that controls are in place limiting access to student records as appropriate.
What are the IAM Compliance Requirements for the General Data Protection Regulation (GDPR)?
A robust IAM solution that satisfies the GDPR compliance requirements for data privacy and security must include:
- Access Management
- Access Governance
- Authorization
- Authentication (including multi-factor authentication)
- Identity Management (IDM)
- Identity Governance
Key to the satisfaction of GDPR compliance requirements is data protection. Consumers retain the right to deny or revoke the collection of their data. An IAM solution that monitors user access to customer identity information and personal data is not enough. For GDPR compliance, an IAM solution must track all access to personal data collected, and update access rights based on both organizational changes and relevant customer preferences.
Resources


