APPLICATION ACCESS GOVERNANCE FEATURES
Reduce Access Risks With Cross-Application Control
Saviynt Application Access Governance (AAG) provides fine-grained visibility across your application ecosystem and out-of-the-box controls to manage access & internal fraud risks.

Cloud Innovation Meets
Application Governance
Centralize fine-grained entitlement management across applications
Automate lifecycle tasks make cross-application provisioning easier and more efficient
Connect security roles to security tasks automatically with out-of-the-box rulesets
Centralize SoD violations visibility across disparate application security models
Discover risky entitlement configurations with proactive environment scans
Take action with prioritized, real-time risk dashboards for investigations
Manage & remediate app risk with the Risk Workbench
Accelerate implementation & adoption with a modern user experience
WHAT YOU CAN DO
Stop SoD Violations in Their Tracks
Significantly reduce internal fraud risk and SoD violations to meet continuous compliance
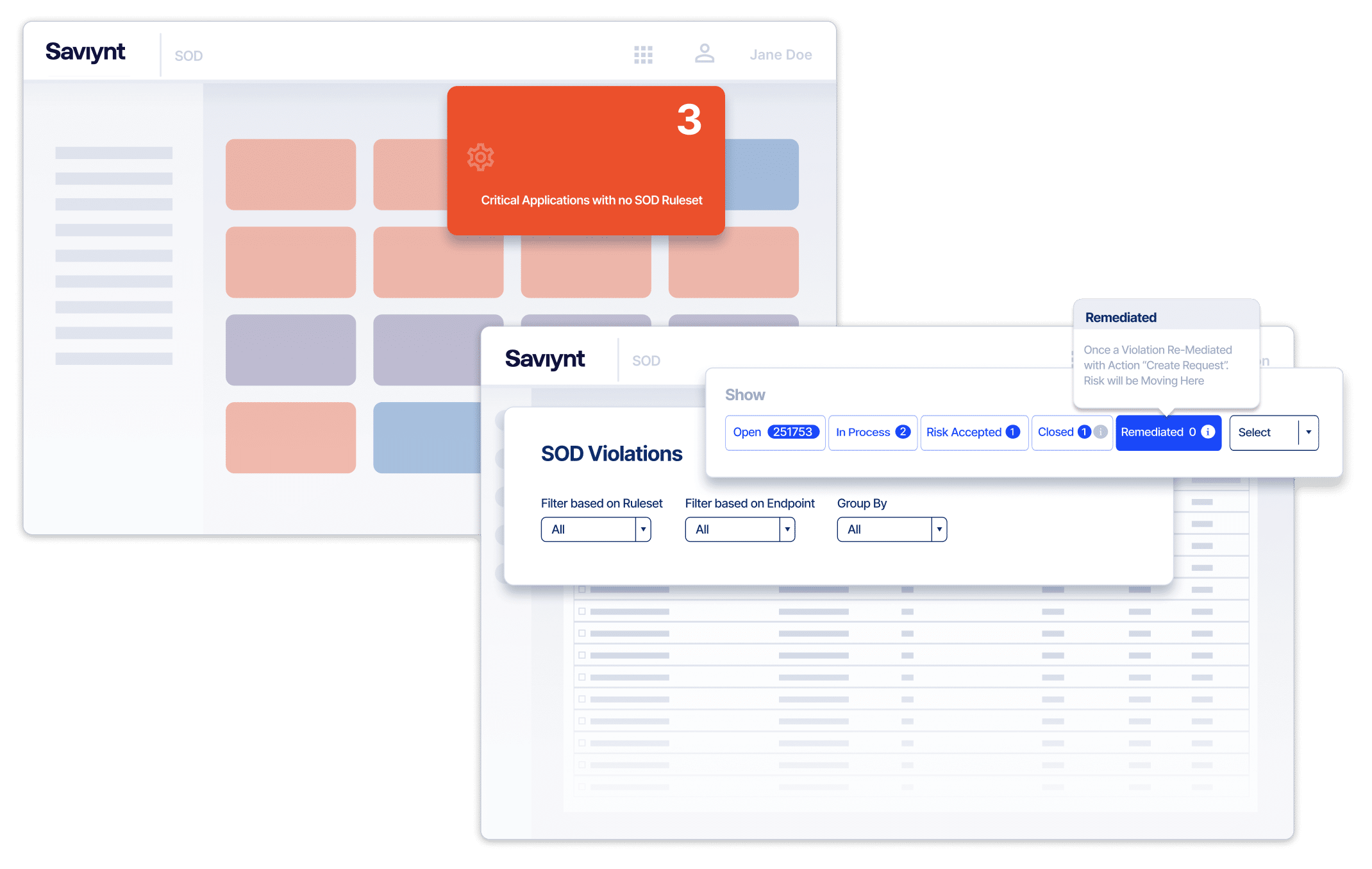
Key Capabilities
- Cross-application SOD
View risk analysis with real versus potential risks - Out-of-the-box SOD Rulesets
Enable rulesets aligned to industry compliance frameworks
- Automatic persistent controls monitoring
- Visibility into actual SoD and key control violators
Get Proactive with Intelligent Requests
& Preventative Risk Analysis
Identify risks before they become problems
Key Capabilities
- Access From Anywhere
Initiate access requests via ServiceNow, the Saviynt mobile app, or a web browser for frictionless access - Access Risk Visibility
Assess access requests to identify anything anomalous or risky SoD and policy violations - Continuous Entitlements Monitoring
Compare peer group analytics to identify outliers
- Risk-based access reviews
- Auto-approval & provisioning of low-risk entitlements
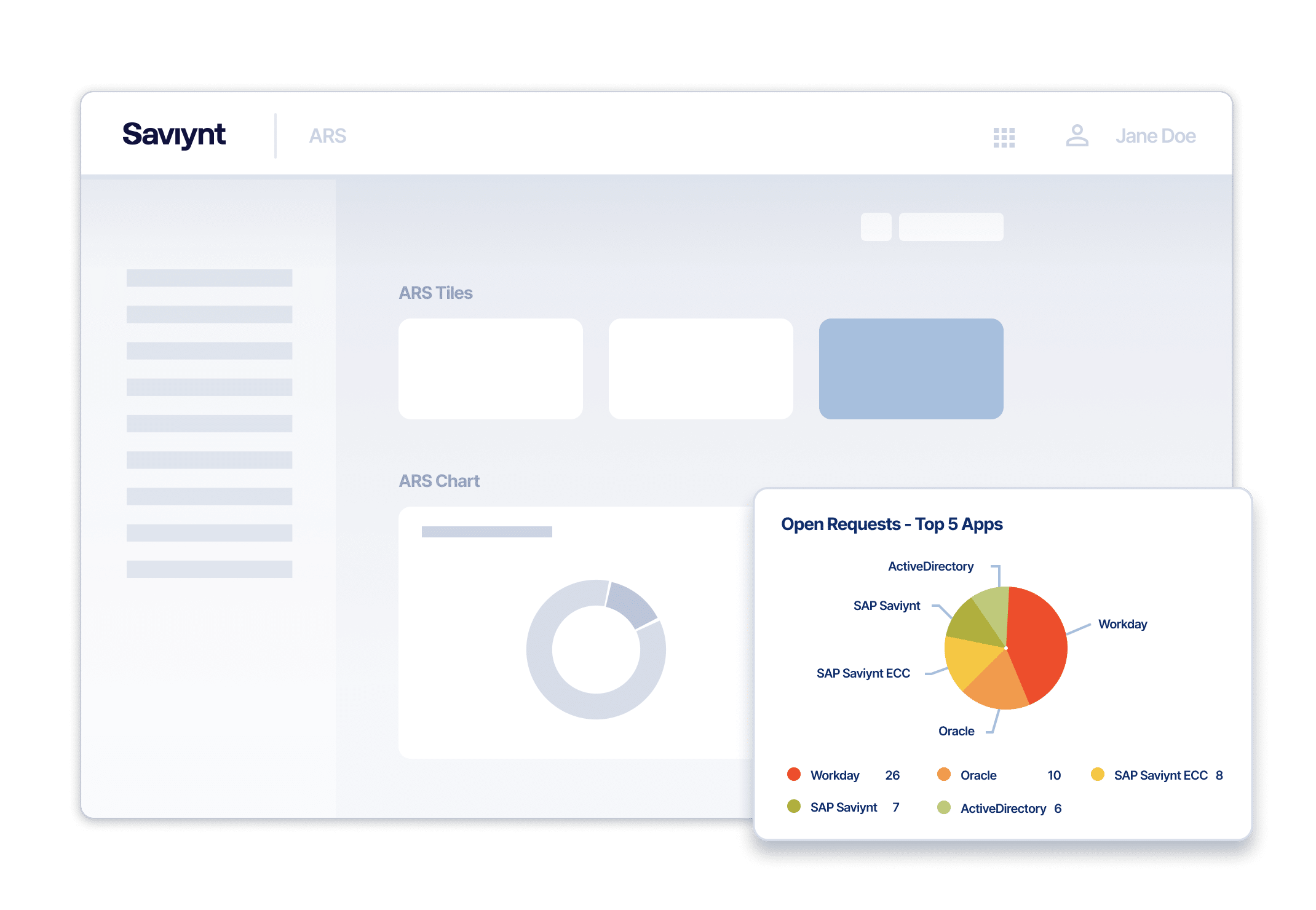
Provide the Right Access at the Right Time
Provide appropriate access to the right people every time with emergency management
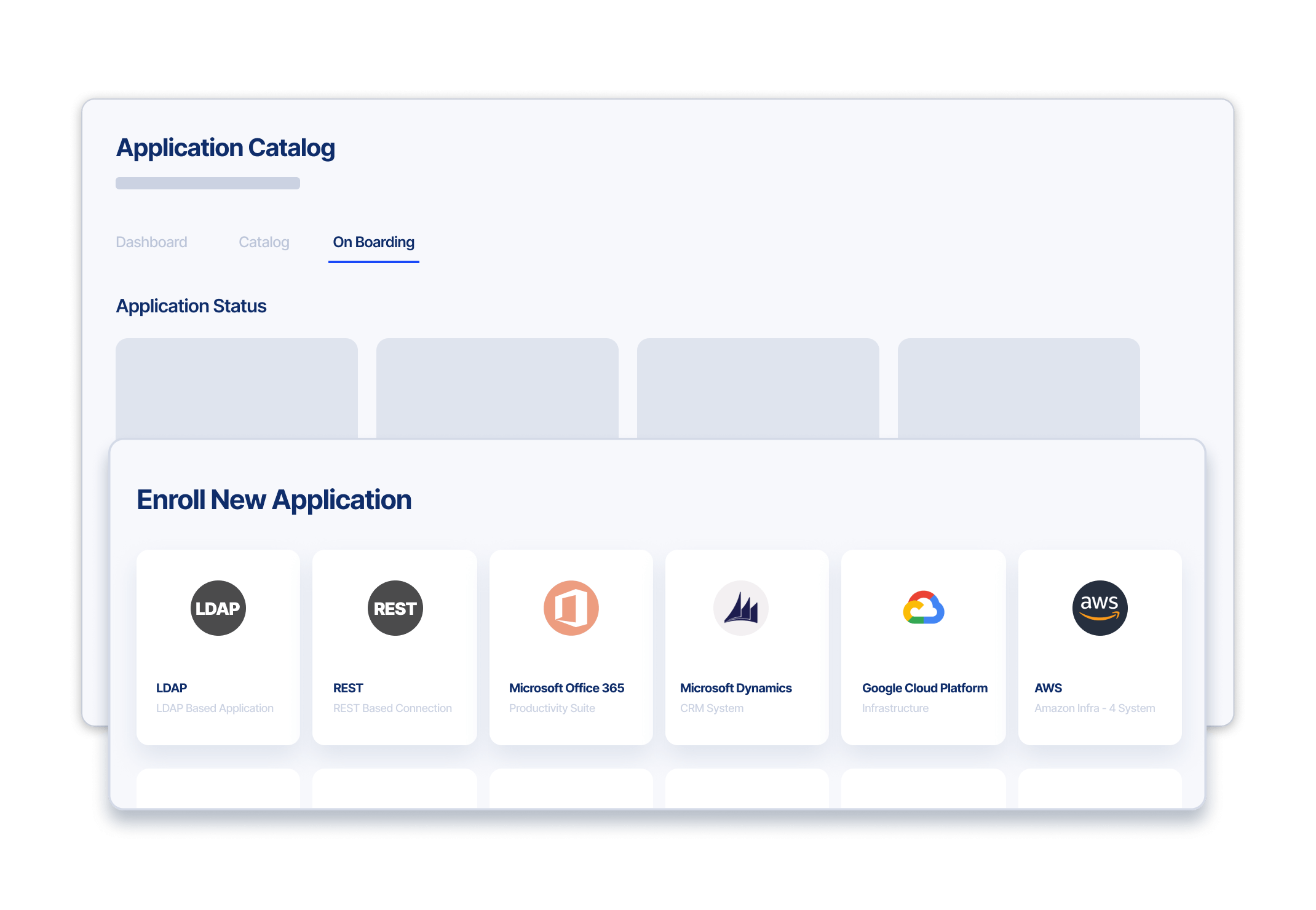
Key Capabilities
- Just-in-time Access
Grant users elevated privileges for a limited time - Session Management and Monitoring
Provision, record, and de-provision privileged sessions - Time-bound Access
Automatically remove access to avoid orphan identities
- Documentation to support audit preparation
- Analytics support proactive session monitoring
- Actionable controls to accept or deny non-compliant commands
Control Monitoring That Never Sleeps
Gain security confidence with control over compliance
Key Capabilities
- Real-time Violation Checks
Quickly isolate and remediate potential violations - Out-of-the-box Controls Library
Save time with compliance controls aligned with industry standards and regulations - Usage Analytics
Manage identity, security, and compliance controls
- Mitigating controls to correct violations
- Evidence reporting to prove compliance status
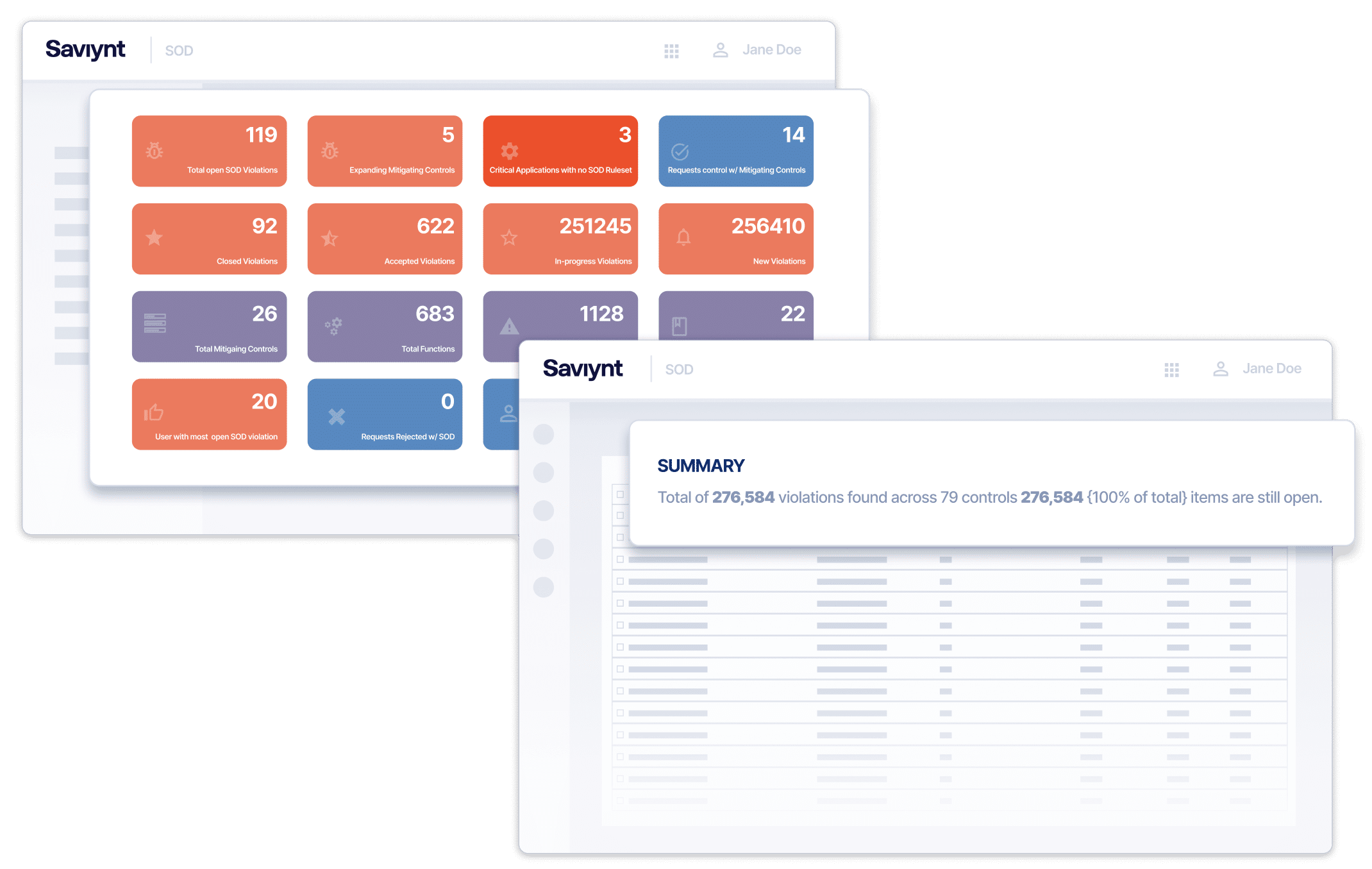
Role Engineering Made Easy
Develop application access for each role automatically
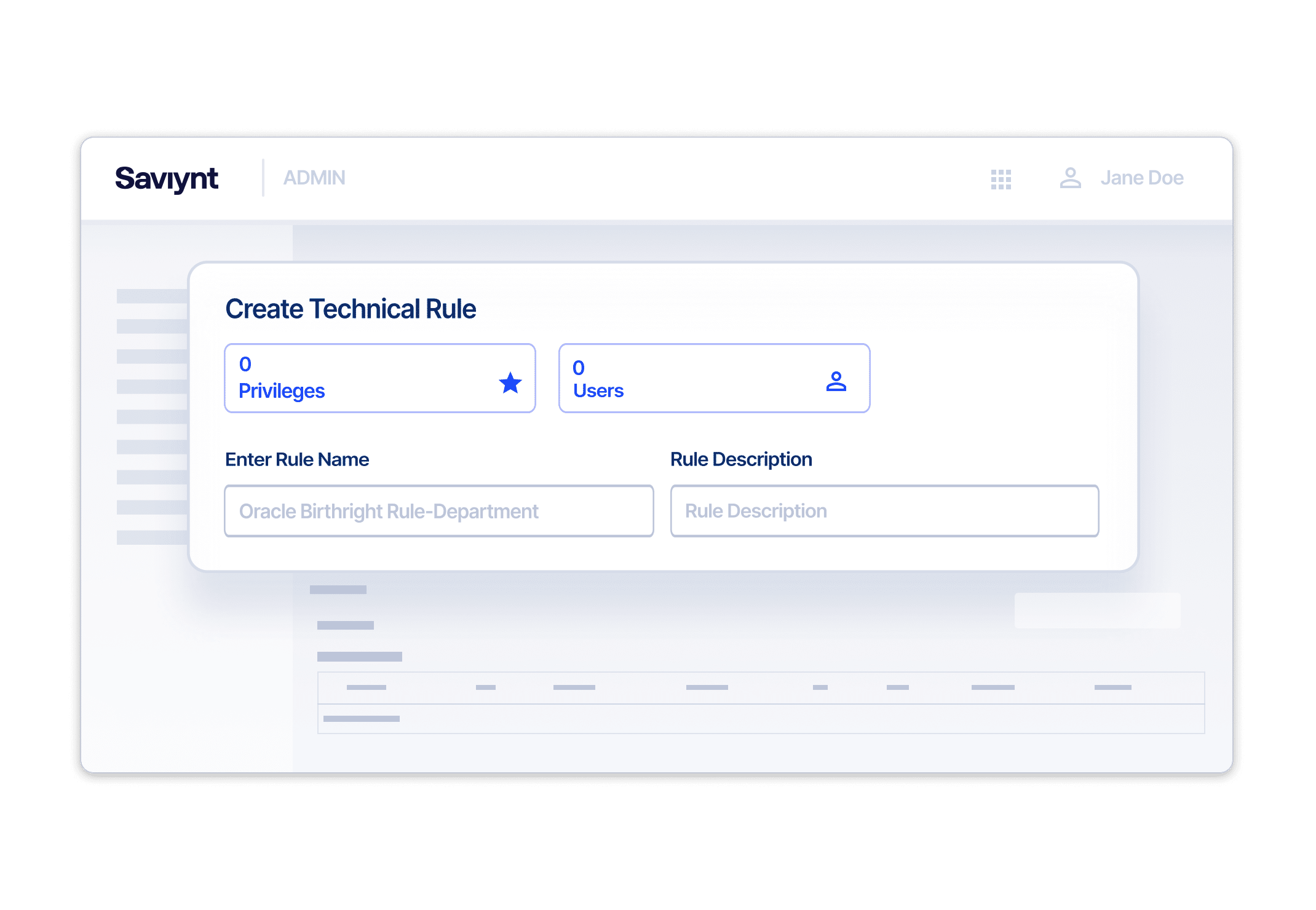
Key Capabilities
- Dynamic Privilege Design & Creation
Use rules and attributes to dynamically assign access - Automated Role Provisioning
Group entitlements to roles to improve provisioning efficiency - Current Application Roles Discovery
Simplify role definition with real-time usage data
Additional Capabilities
- Visibility to whether entitlements within roles are being used
- Recommendations to help improve, delete or consolidate roles to limit sprawl
- Role management and what-if analysis