INTEGRATION
Saviynt for Google Cloud Platform Security & Compliance
Achieve Zero Trust across your Google Cloud ecosystem

Managing risk in GCP requires control over users, machine identities, and privileged access.
Saviynt’s Enterprise Identity Cloud bolsters security controls and facilitates Zero Trust with unified, best-in-class identity governance and privileged access capabilities
Identity & Mitigate Security Risks
Gain visibility, remediate risks, and enforce least privilege model
Simplify Privileged Access
Continuously discover, onboard, and manage privileged access for GCP
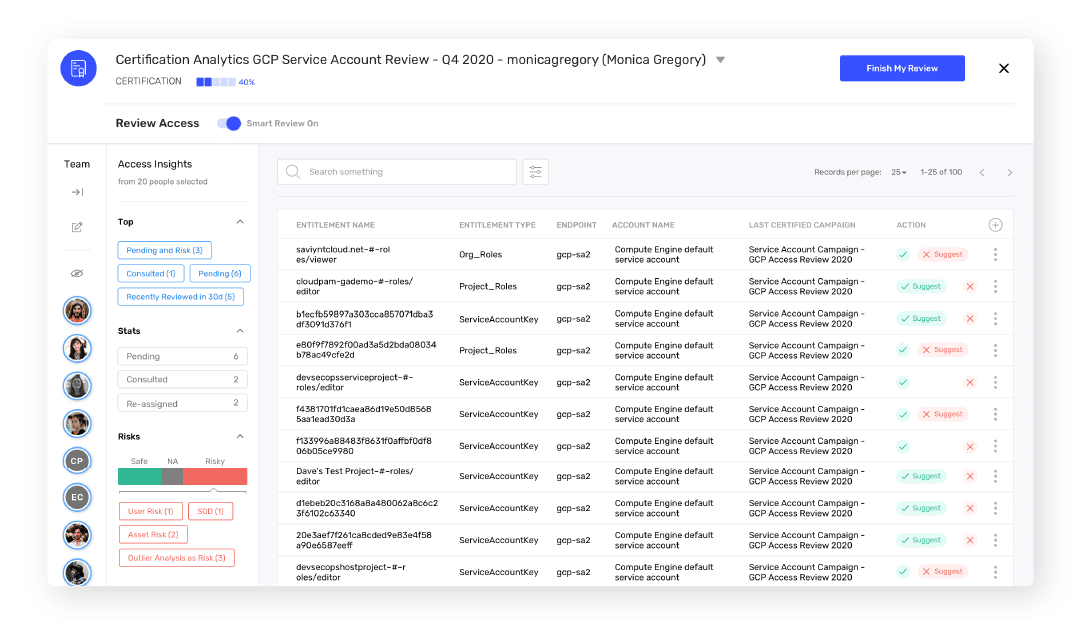
Automate Identity Workflows
Streamline access lifecycle and governance to create “right-sized” access
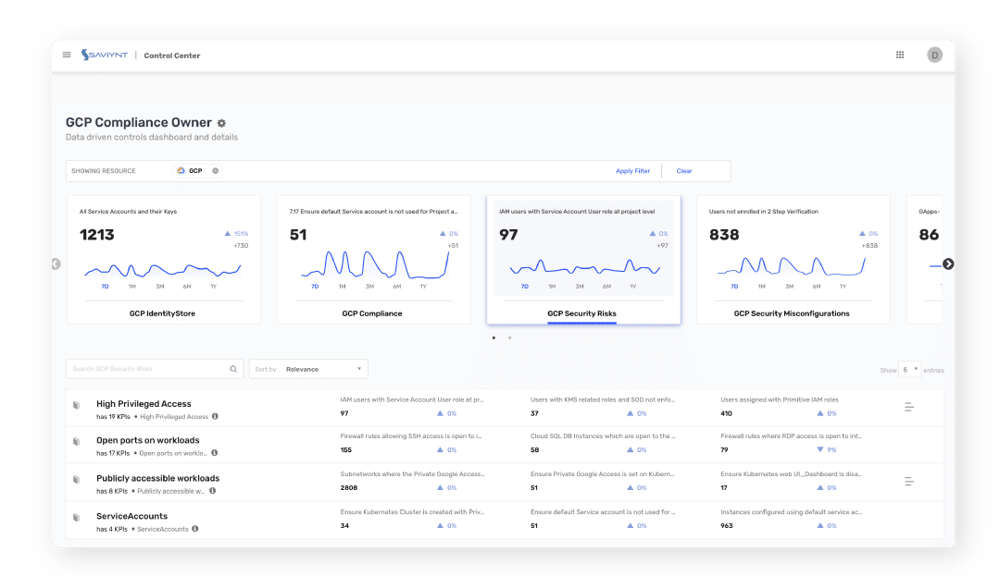
Uncover Security Risks in Real Time
- Discover configuration and security risks across virtual machines, databases, and cloud assets
- Use 250+ preset security controls and risk signatures – or define your own IAM policies
- Continuously monitor your security posture against compliance frameworks
- Automate account and role least privilege and prevent configuration drift
Protect Privileged Accounts
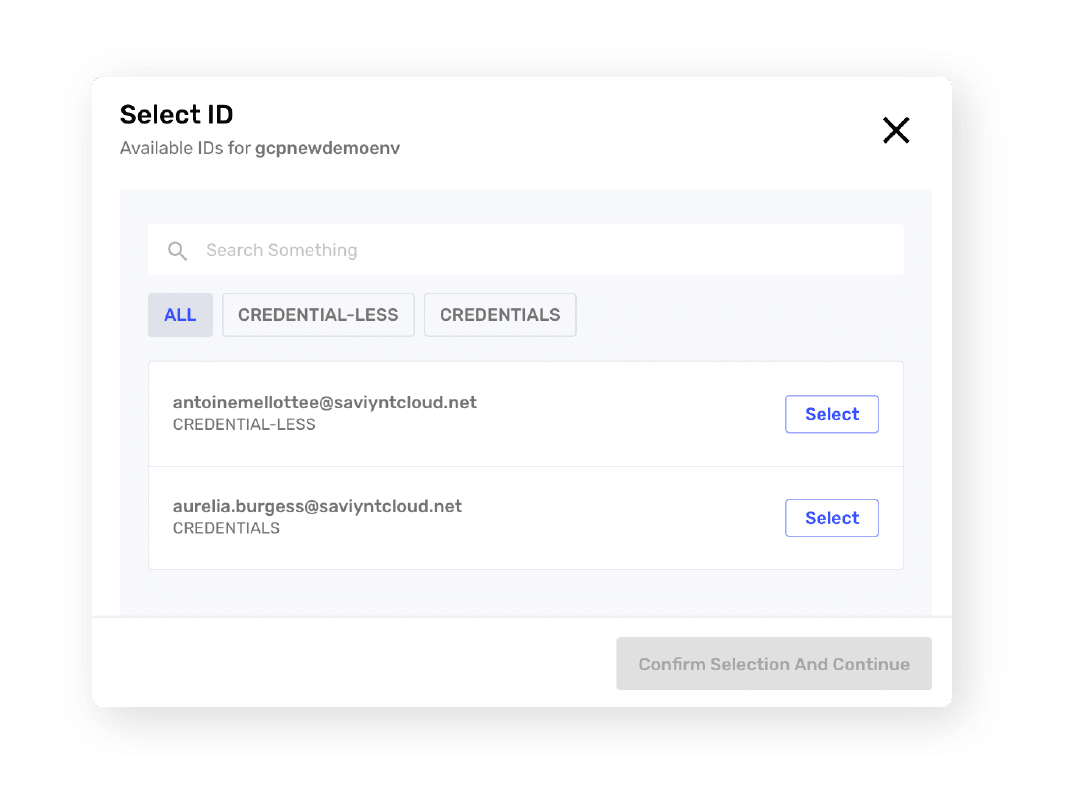
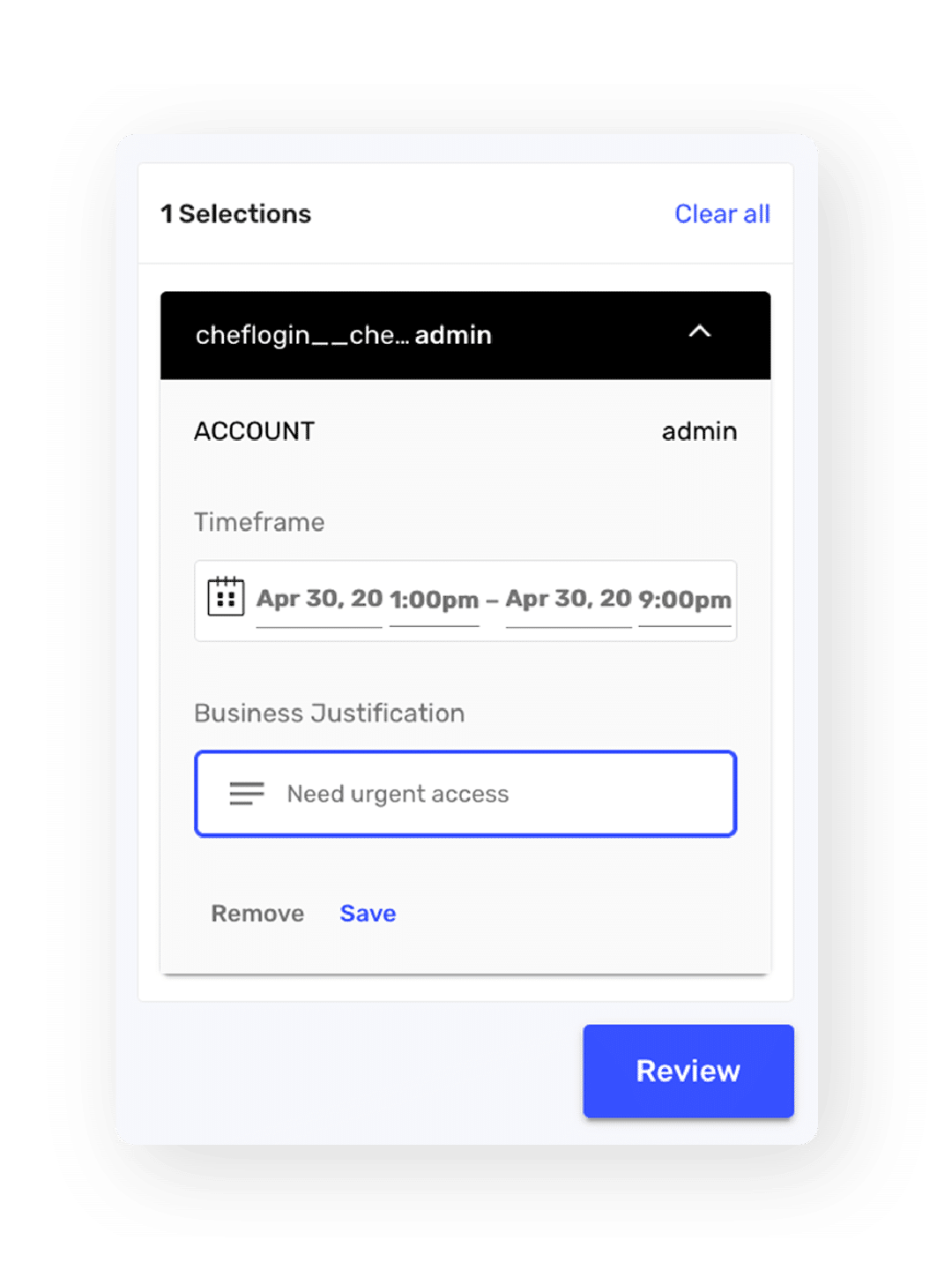
- Discover and onboard new privileged accounts, applications, and workloads
- Manage workload, database, and console privileged accounts
- Mitigate risk with preventive actions and FedRAMP compliance controls
- Assign IDs, ownership, and succession policies to service accounts
Secure DevOps and the CI/CD Pipeline
- Automate repetitive tasks and provide privileged account access with RPA bots
- Eliminate hard-coded credentials with just-in-time workload credentials or service account keys at code execution
- Reduce key exfiltration and compromised account risk