What is Privileged Access Management (PAM)? A Complete Guide for 2026

If you are researching Privileged Access Management, you are trying to answer a simple but high-stakes question.
How do we control the accounts that can do the most damage if they are compromised?
In 2026, that question is bigger than ever. PAM is no longer a password vault problem. It is a standing privilege problem in a world dominated by cloud infrastructure, machine identities, and AI-driven automation.
This guide breaks down what PAM actually is, why it matters now, and how modern organizations should think about it.
Key Takeaways
- Privileged Access Management (PAM) controls and eliminates standing admin privileges by enforcing least privilege and Just-in-Time (JIT) access to reduce breach impact.
- Modern PAM goes beyond password vaults, securing both human and machine identities across cloud, CI/CD, and AI-driven environments.
- Zero Standing Privilege dramatically reduces ransomware and lateral movement risk by shrinking the attack window from months to minutes.
- PAM is most effective when integrated with Identity and Access Governance (IGA) and Identity Security and Posture Management (ISPM), forming a single identity security strategy for 2026 and beyond.
What is Privileged Access Management?
Privileged Access Management (PAM) is a cybersecurity discipline that controls, monitors, and eliminates standing administrative privileges. PAM does this by granting temporary, task-based access to sensitive systems and data.
PAM protects accounts with elevated permissions. These are the accounts that can change system configurations, access sensitive databases, deploy production code, or delete critical infrastructure.
Modern PAM is built around two core principles:
-
Principle of Least Privilege (PoLP): Users receive only the minimum access required to perform a specific task.
-
Just-in-Time (JIT) access: Elevated access is granted temporarily and automatically revoked upon task completion.
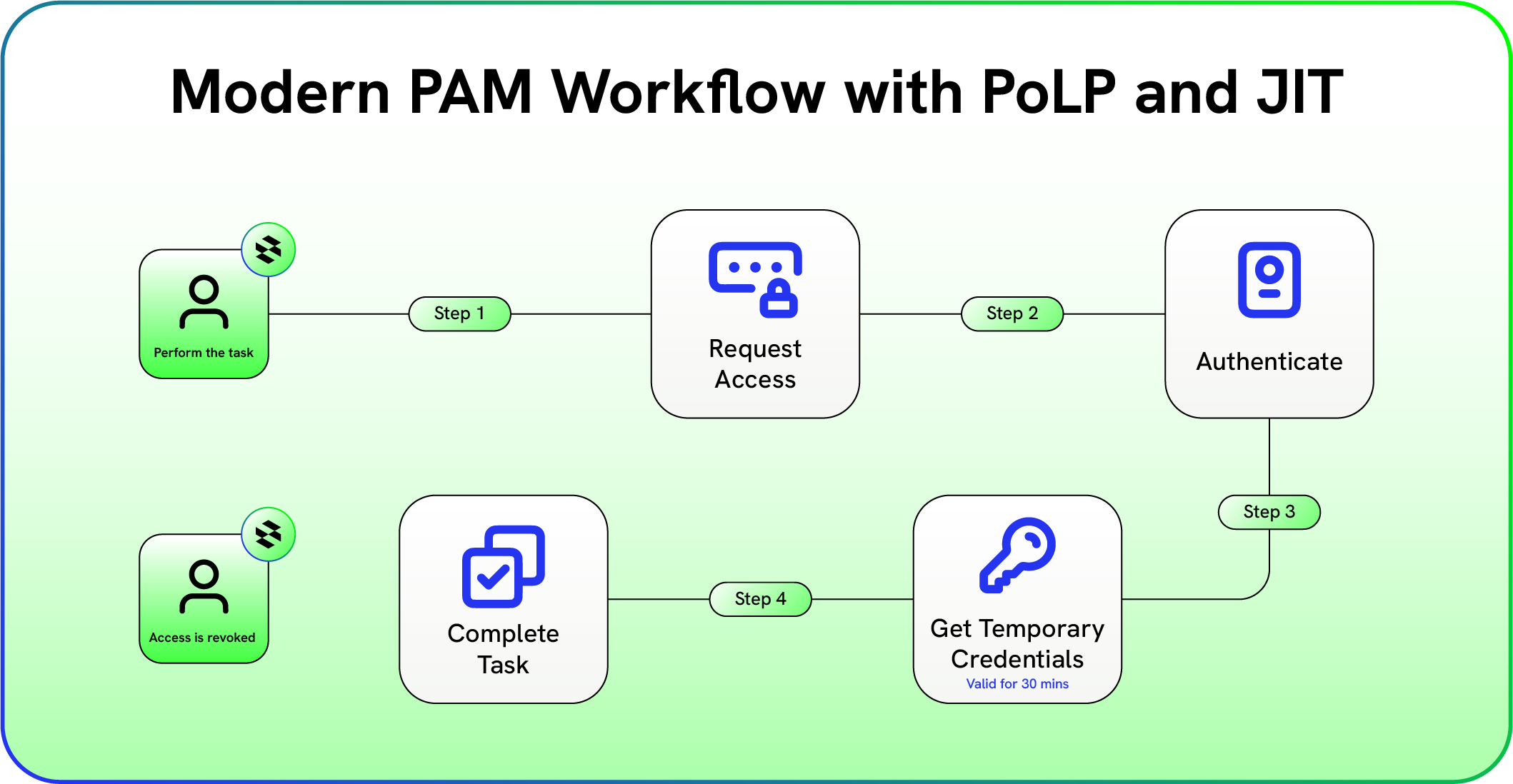
The goal is to remove permanent administrative access that attackers love to exploit. If an attacker compromises a low-privilege account, the blast radius is limited. But if they compromise a standing admin account, the consequences are severe.
In most enterprise environments we walk into, uncontrolled privileged access is still one of the largest unmanaged security risks; teams are often surprised by how much exposure they actually have.
PAM in 60 Seconds
If you only remember a few things about PAM, remember these:
-
Privileged Access Management controls access to high-risk administrative accounts.
-
Modern PAM eliminates standing privilege through temporary access.
-
PAM protects both human and machine identities.
-
PAM reduces ransomware and lateral movement risk.
-
Privileged Access Management works best when integrated with identity governance and administration (IGA) and identity security posture management (ISPM).
-
Cloud native PAM scales with modern infrastructure and AI workloads.
Bottom line: PAM is about shrinking the attack window from months to minutes.
Why PAM Used to Be Simple (And Why It Isn't Anymore)
Ten years ago, PAM was relatively straightforward. You had a handful of system administrators who needed root access to on-premises servers. You stored those privileged credentials in an encrypted vault, rotated passwords regularly, and called it a day.
That world is gone.
Three major shifts have completely transformed what privileged access management needs to address. They are:
The Death of the Network Perimeter
Hybrid and cloud native environments erased the idea of a safe internal network. Applications now span AWS, Azure, Google Cloud, and on-premise systems. Employees work from anywhere, and infrastructure is provisioned through code, which changes constantly.
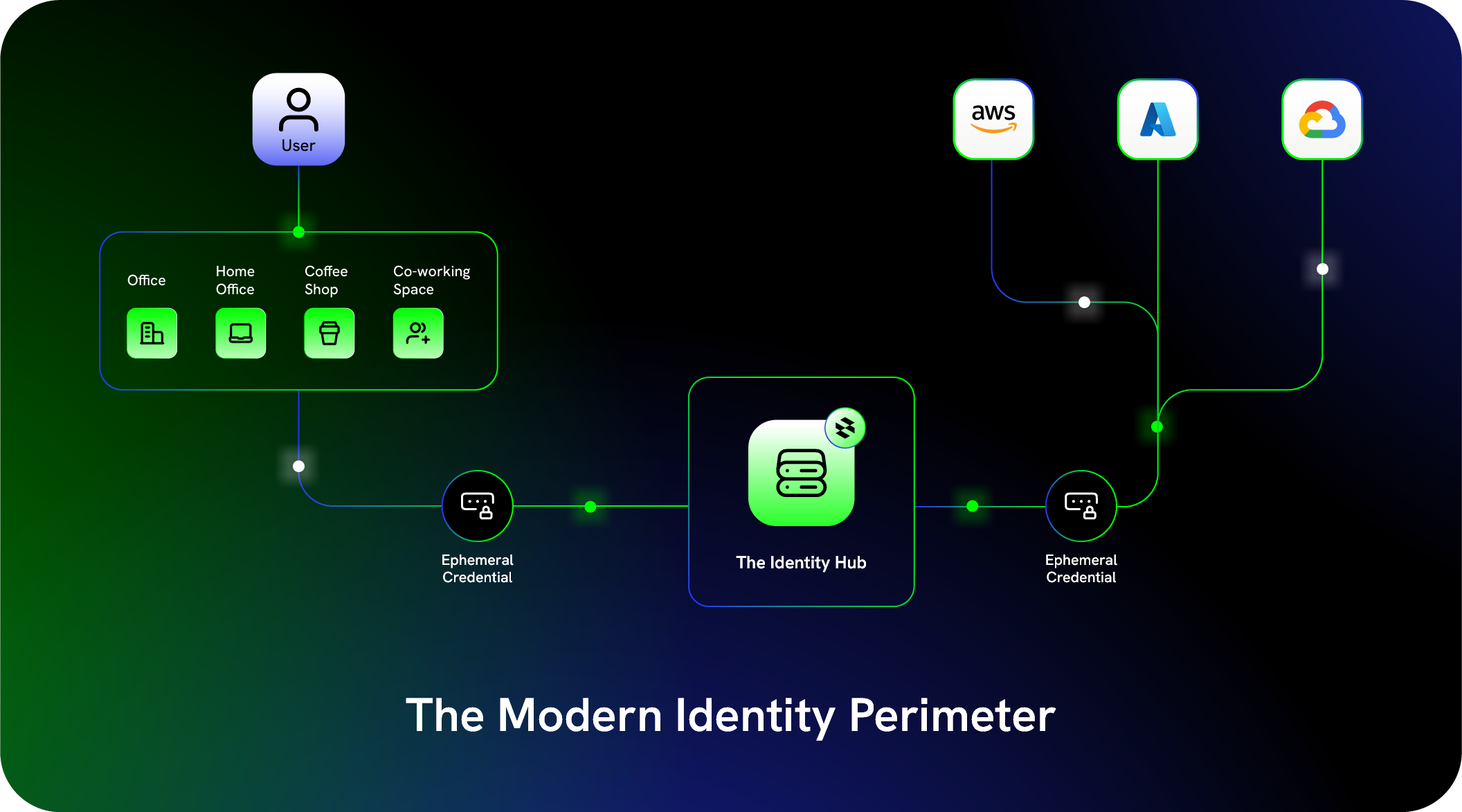
Static credential vaults cannot keep up with dynamic environments where resources appear and disappear in minutes.
Bottom line: Access is everywhere and constantly changing. PAM must be dynamic.
The Identity Explosion (It's Not Just Humans Anymore)
A stat that makes every CISO nervous is that machine identities are estimated to outnumber human identities in most enterprise organizations by roughly 80 to 1.We're talking about:
- API keys that let services talk to each other
- Service accounts that run background processes
- OAuth tokens that enable application integrations
- AI agents that autonomously perform tasks
- CI/CD pipeline credentials that deploy code
Most organizations cannot confidently inventory these identities, let alone manage them. Forgotten credentials accumulate permissions over time, creating a large, invisible attack surface.
At the same time, privileged access is no longer limited to IT administrators. Business users, contractors, and developers often hold elevated permissions to critical systems.
Bottom line: PAM must scale beyond human admins to manage machine identities and distributed access.
Standing Privileges: The Permanent Security Liability
Persistent administrative accounts create permanent targets. Attackers do not need to break into a vault if they can escalate privileges from a compromised endpoint.
Standing privilege extends the attack window indefinitely. Every persistent admin account is an open invitation that never expires. Modern PAM exists to close that door.
Bottom line: Every persistent admin account increases long-term risk.
Modern PAM Moves From Password Vaults to Zero Standing Privilege
The shift from vault-based PAM to cloud native Zero Standing Privilege models is not incremental. It is architectural.
| LEGACY PAM | MODERN PAM |
| Static, long-lived credentials | Ephemeral, task-based credentials |
| Vault-centric architecture | Zero Standing Privilege model |
| Focused on human administrators | Designed for human and machine identities |
| On-premises infrastructure | Cloud native SaaS delivery |
| Reactive credential protection | Proactive posture management |
Instead of storing long-lived passwords, modern PAM provisions short-lived credentials that expire automatically after a task is completed. For example, an engineer may request temporary access to restart a production server, receive credentials valid for a limited session, complete the task, and lose access automatically.
Bottom line: Modern PAM removes permanent backdoors and dramatically shrinks the attacker’s opportunity window.
PAM, IGA, and ISPM: Better Together
What some vendors won't always tell you upfront is that PAM works best when it's not isolated. A mature identity security strategy converges three disciplines:
-
Privileged Access Management: Controls who can do what with elevated permissions
-
Identity Governance and Administration: Manages access reviews, certifications, and segregation of duties to ensure compliance.
-
Identity Security Posture Management: Continuously monitors your identity environment to identify risks, misconfigurations, and anomalies
Think of PAM, IGA, and ISPM this way:
-
PAM controls the key to the front door
-
IGA makes sure the right people have the right keys for the right reasons
-
and ISPM watches the entire operation to spot problems before attackers do.
Organizations that deploy PAM as a siloed tool usually discover the hard way that vaulting credentials alone does not equal identity security.
Bottom line: Converged identity security delivers stronger protection than isolated tools.
Why PAM Matters Right Now
The urgency around PAM isn't hype. It's driven by real attack patterns.
Human Identity Attacks
Your employees and contractors are targets for phishing campaigns that are more sophisticated than ever. Add to that social engineering and weak, reused passwords, and you have a real problem.
When an attacker compromises a human identity with standing administrative privileges, they gain a foothold that can be exploited for months before being detected.
It’s not all doom and gloom because there is a solution. Implement time-limited, request-based access. No one has standing admin rights, and every privileged action requires justification and approval, generating an audit trail.
Machine Identity Sprawl
Remember that 80:1 ratio? Most organizations have no comprehensive inventory of their machine identities.
API keys sit in old repositories, forgotten by developers who've moved on. Service accounts are just hanging out, accumulating countless permissions over years. OAuth tokens never expire.
The big problem is that these non-human identities are often unmonitored, unrotated, and unprotected. All that “un” is the recipe for undoing! These are precisely the credentials attackers actively hunt for because they're easier to exploit and harder to detect than compromised human accounts.
Agentic AI
Agentic AI is new and evolving quickly. Autonomous AI agents are being deployed to handle tasks like customer service, data analysis, report generation, and even code deployment. Each agent needs access credentials. Traditional vault-based PAM can't manage ephemeral, purpose-bound credentials at the scale and speed AI agents require.
If your organization is deploying AI agents (or planning to), you need a PAM strategy that can provision temporary, narrowly scoped credentials on demand, and revoke them the moment the task completes.
Bottom line: Emerging technology increases the need for dynamic privileged access controls.
How PAM Prevents Ransomware (And Other Attacks)
Let's talk real-world impact. How does PAM actually stop attacks?
Ransomware attacks typically follow a pattern: initial access → privilege escalation → lateral movement → data encryption.
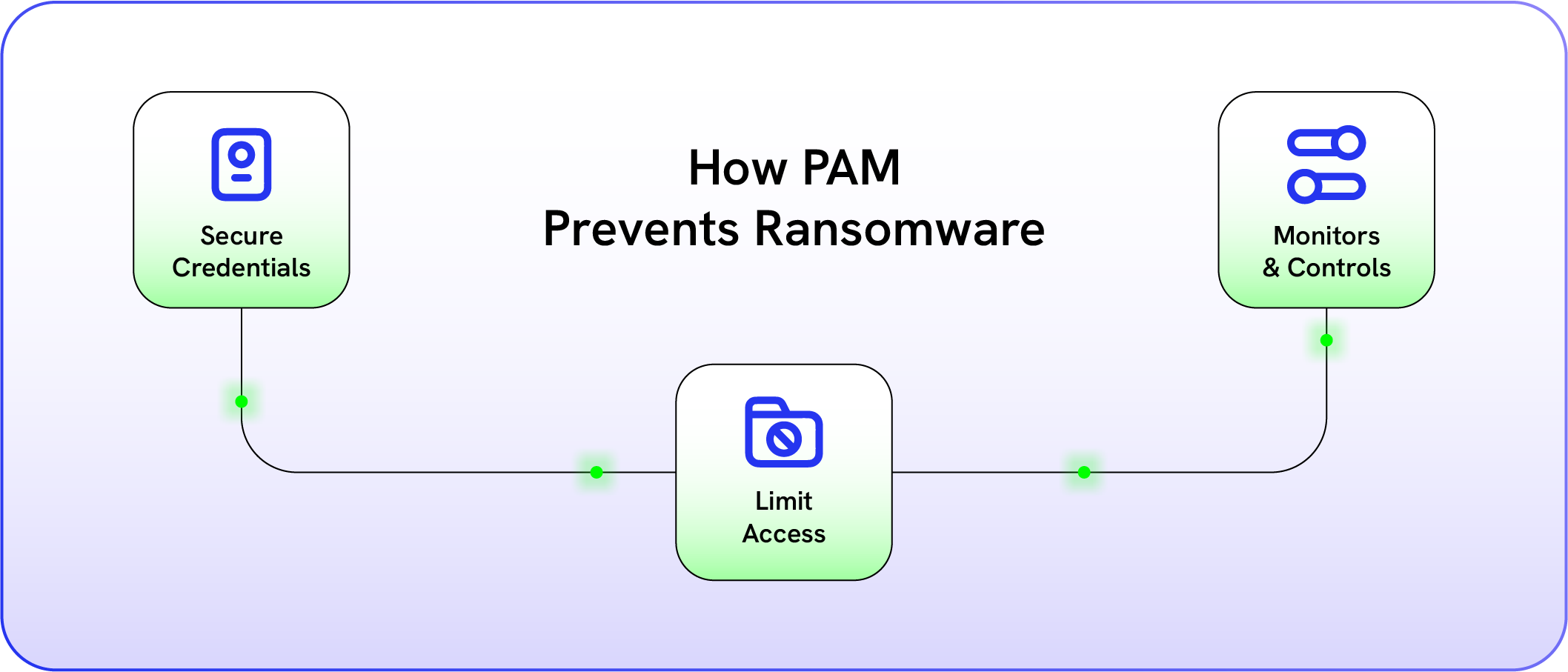
PAM disrupts this chain at multiple points.
-
Initial Access: Even if an attacker compromises a user account through phishing, that account has minimal privileges. Without standing admin rights, the attacker can't immediately move to high-value targets.
-
Privilege Escalation: With proper PAM, there are no local admin rights to steal. Every privileged action requires authentication and generates logs, making silent escalation nearly impossible.
-
Lateral Movement: Session Isolation and Zero Standing Privilege prevent the attacker from jumping from a compromised laptop to the data center. Even if they steal a password, it's already expired or it requires additional authentication factors.
What would have been a catastrophic breach becomes a contained incident affecting a single user account.
Bottom line: PAM reduces both the likelihood and impact of ransomware.
What to Look for in a PAM Solution
If you're evaluating vendors, here are three questions that cut through the marketing:
-
Can you actually eliminate standing privilege?
Many vendors tout Just-in-Time access, but their systems still rely on long-lived service accounts running in the background. Ask specifically, "How many persistent credentials exist in your implementation?" If the answer is more than zero, they haven't achieved true Zero Standing Privilege.
-
What's the administrative overhead at scale?
PAM shouldn't require a dedicated team to maintain. Ask about credential rotation processes, session monitoring, and policy updates. If they tell you it depends on your environment without concrete examples, that's a red flag. You want a solution that scales without proportionally increasing your headcount.
-
How does this integrate with your existing stack?
Siloed PAM is a security blind spot. Your PAM solution should share intelligence with your SIEM, integrate with your IGA platform, and work with your existing identity providers. If the vendor can't articulate specific integration points with tools you already use, you're looking at another isolated security island.
The Bottom Line When it Comes to Privileged Access Management
Privileged access management isn't optional anymore—not if you're serious about security. The days of static admin accounts and password vaults are over. The modern threat landscape, the explosion of machine identities, and the rise of agentic AI demand a different approach.
Look for solutions that:
-
Actually eliminate standing privileges (not just claim to)
-
Handle both human and non-human identities at scale.
-
Integrate with your existing security stack.
-
Provide a clear path from where you are today to Zero Standing Privilege.
And remember, PAM is most effective when it's part of a converged identity security strategy, alongside governance and posture management. Don't think of it as just another security tool. Think of it as the foundation for controlling access to everything that matters in your organization.
The credentials attackers want most are the ones they can't steal because they don't exist except for the brief moments they're actually needed. That's the promise of modern PAM, and it's achievable with the right approach.
Frequently Asked Questions About Privileged Access Management
What's the difference between IAM, IGA, and PAM?
Identity and Access Management (IAM) is the foundation. It handles authentication (SSO, MFA) and basic authorization for all users. Identity Governance and Administration (IGA) adds a compliance layer through access reviews, certifications, and segregation-of-duties checks. PAM is the specialized layer for elevated permissions, adding session monitoring, Just-in-Time access, and credential vaulting for high-risk accounts.
How does PAM work with cloud environments?
Modern PAM is built for cloud-first architectures. Instead of extending traditional vault-based approaches to AWS, Azure, or GCP, cloud-native PAM integrates directly with cloud provider identity systems. It can provision temporary cloud credentials, enforce session time limits, and automatically revoke access—all without requiring you to maintain infrastructure.
Can PAM slow down developers and operations?
Only if it's implemented poorly. The right PAM solution should feel nearly invisible to users while maintaining security. Developers request access, get quick approvals for legitimate needs, receive temporary credentials, and continue working. The friction should be measured in seconds, not hours.
Related Post




Report
Saviynt Named Gartner Voice of the Customer for IGA

EBook
Welcoming the Age of Intelligent Identity Security

Press Release
AWS Signs Strategic Collaboration Agreement With Saviynt to Advance AI-Driven Identity Security

Solution Guide