
Accelerate Time to Value and Maximize your Investment
Identity programs shouldn’t be complex. Saviynt is committed to delivering shorter Time to Value (TTV) to customers and maximizing their investment in Saviynt. We have designed Expert Services offerings to do exactly this.
Plan
Understand Saviynt product capabilities and get a customized success plan that is tailored to your business needs
Advise
Expert advice on Saviynt best practices and implementation methodology to attain TTV
Learn
Access to thought leadership and learnings from complex identity problems across industry verticals
Monitor
Regular health checks and tailored release notes customized to your implementation roadmap
Trusted Enterprise Partners
Accelerate your identity security initiatives
with the best in the business

%20(1).png?width=154&height=131&name=PwC_Logo%20(1)%20(1).png)
Choose the right service
engagement for you.
Success Package
With our success package, you’ll get direct access to a Saviynt Platform Expert who will guide you through each step of your journey to a successful identity governance program.
Our experts will help you:
- Access quick start guides and onboarding documentation
- Learn more about Enterprise Identity Cloud’s (EIC) capabilities
- Learn more about connectors and our connector framework
- Gain insights into best practices, tips and tricks, and more
Learn more about what’s included in our Success Package:
Saviynt Instance Provisioning
Kick Off
Success Plan
Expert Review
System Health Review
Saviynt instances is handed over to customer.
Ideal within first week of purchase.
Description: Engagement Kick off to introduce Saviynt Customer Success team, review capabilities purchased and review engagement mode
Ideal within first week of purchase.
Description:
- Review customer’s adoption roadmap and advise on the best practices OR
- Review requirement document for an implementation phase and provide feedback if requirements are in alignment with industry standards and Saviynt product capabilities
Deliverable:
- Value Adoption Plan
- Requirement Review Document
Ideal within 4 weeks of purchase.
Description: Review Key milestones, bring extensive knowledge of solving complex problems
- Review Design Document to align with the Saviynt best practices
- Review implementation and provide guidance to avoid common problems
- Review Deployment Plan for better success rate and avoid surprises
Deliverable:
- Design Review document with risk rating and impact of findings
- Configuration assessment report
- Deployment Review document
Description: Review the overall health of the Saviynt platform, identify common problems and provide remediation path
Deliverable:
- System Health Review Document
Ideal within first week of purchase.

Time to Value Package
Based on our experience of numerous implementations, we’ve identified a collection of use cases that will help you to attain quicker TTV and ROI. Whatever your business priority is—compliance, Identity Lifecycle Automation, Privilege Access or Governing External Identities–we have a solution for you. Our commitment to you is to attain value in less than 12 weeks.
Choose the right service engagement for you:
Plan
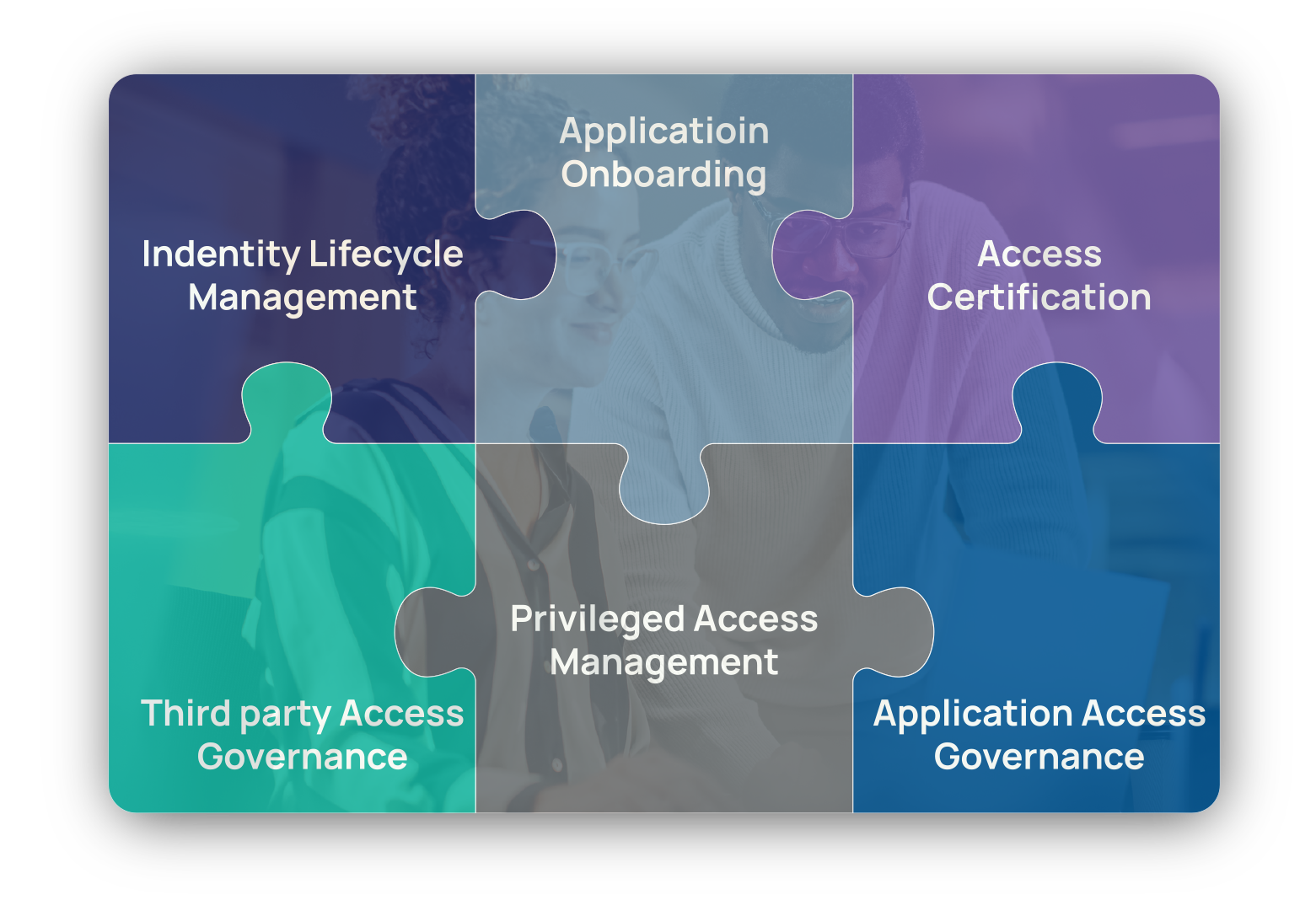
IGA Quick StartSave cost by automating the identity lifecycle events and provisioning to key enterprise Apps and platform.
- Connect with 5 Apps
- Zero day access
- Automated provisioning
- Access reviews
- Risk based access approvalsIGC access control
Advise
Enable key compliance controls to manage and govern user access across your enterprise.
- Import access of 5 Apps
- Import access glossary
- Access review controls
- ITGC access controls
App Access GOV
Prevent toxic combinations and reduce internal fraud by enabling integrated SOD risk approval and review
- Prevent toxic combinations and reduce internal fraud by enabling integrated SOD risk approval and review
- Connect with 1 premium App
- Preventative & detective SOD violation controls
- Automated access provisioning
- Access reviews
PAM for Cloud Assets
Secure cloud workloads and get visibility into high risk assets.
- Connect with 1 account (AWS, GCP or Azure)
- Continuous workload discovery
- Just in time access (compute)
- Session recording
- Visibility into cloud assets
PAM for On-Prem Assets
Secure on-prem workload with industry leading identity product.
- Bootstrap 500 on-prem workloads (Window, Linux, DBs)
- Privileged credential mgmt
- Just in time access
- Windows session management
- Session recording
- Risk based access approvals
3rd Party Access GOV Quick Start
Govern third party identities and organizations through centralized access policies.
- Invitation or form based identity onboarding*
- Identity approval workflows
- OOTB company delegated administration use cases*
- Automated lifecycle events
- Centralized access controls & policies
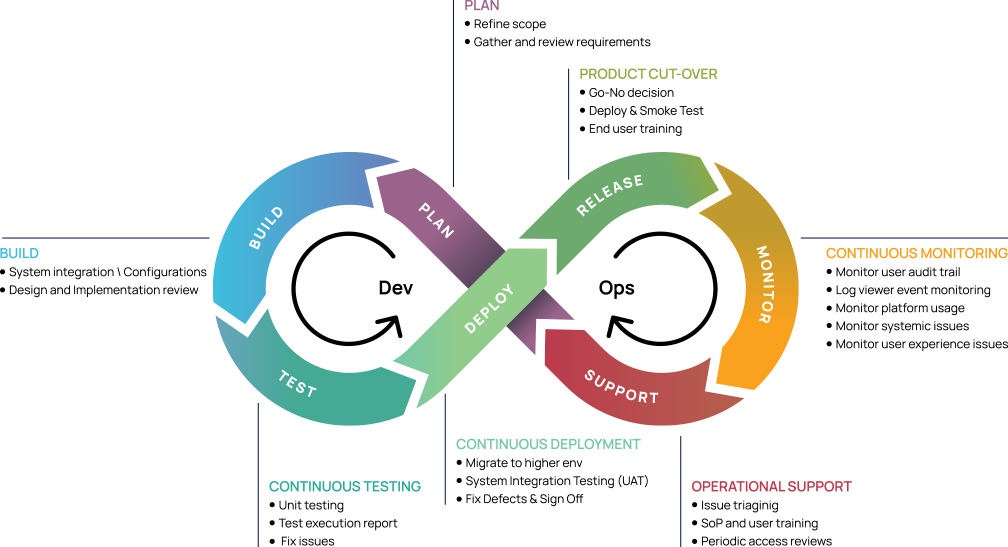
Execution Model to Deliver TTV
The best approach to solve a complex problem is by breaking it down into smaller logical steps and then bringing the pieces of the puzzle together. With the multiple decades of experience in the Identity domain and solving a vast range of problems across industries we advise customers to adopt an agile model that delivers continuous incremental business value. This model encapsulates the feature growth and operationalization of the Saviynt Identity Cloud platform with each step.
Saviynt Experts
have curated industry specific use cases and defined a delivery model that accounts for the complexity of businesses of various sizes.
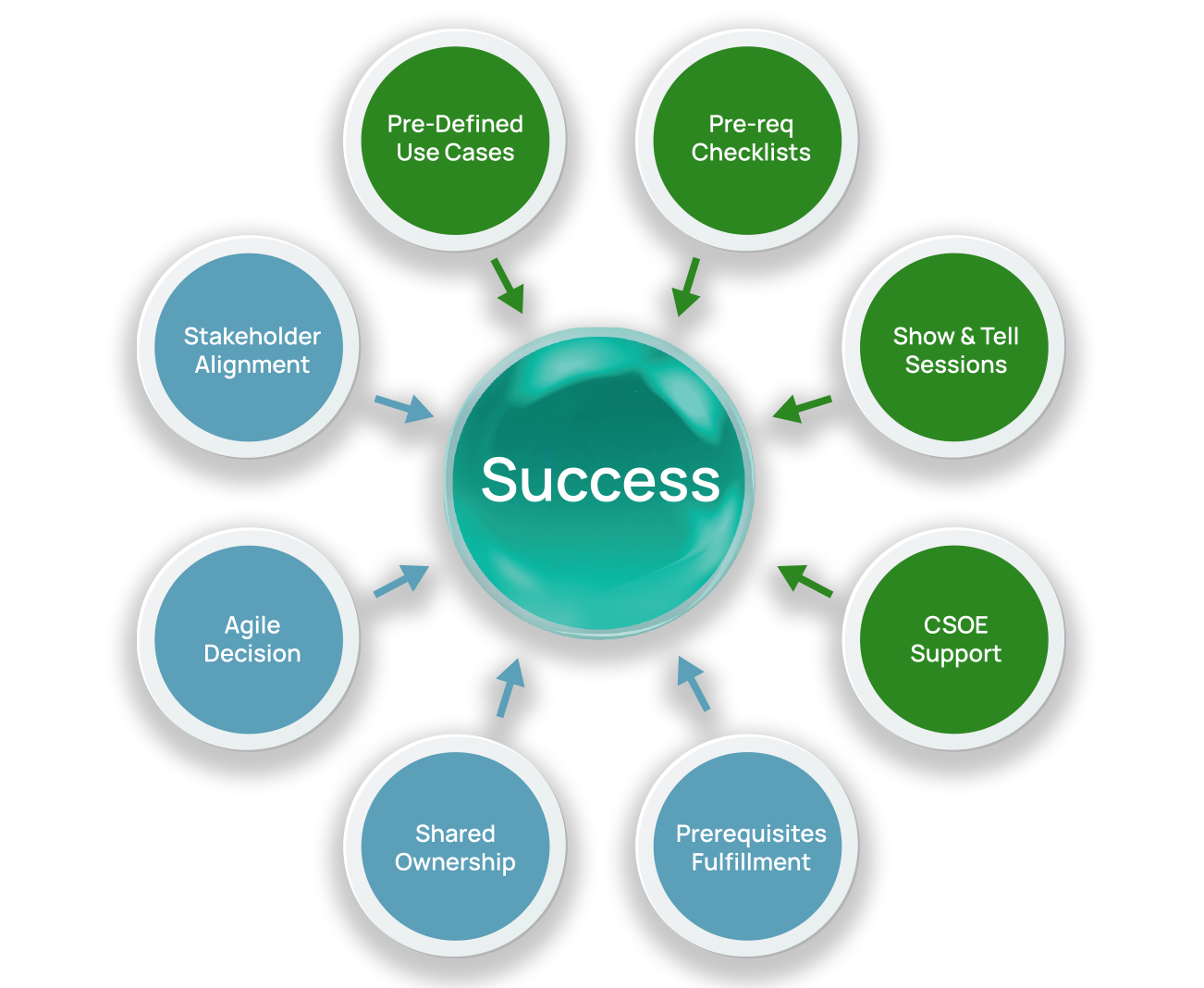
- Pre-selected Use Cases to limit scope creep and avoid requirements discovery delays
- Pre-req Checklists will be shared with the customer so that customers can line up resources and make any requests in advance.
- Show and Tell Sessions where Saviynt will walk-through the steps and configurations to implement specific use cases.
- Shared Ownership Model where Customer Team will try implementing the solution with guidance and review by Saviynt team through Office Hours / Review sessions. If customer team is unable to finish an integration / use case in a predetermined time, Saviynt team will pick up and finish the implementation
- Agility in decision making and on-time prerequisite fulfillment.
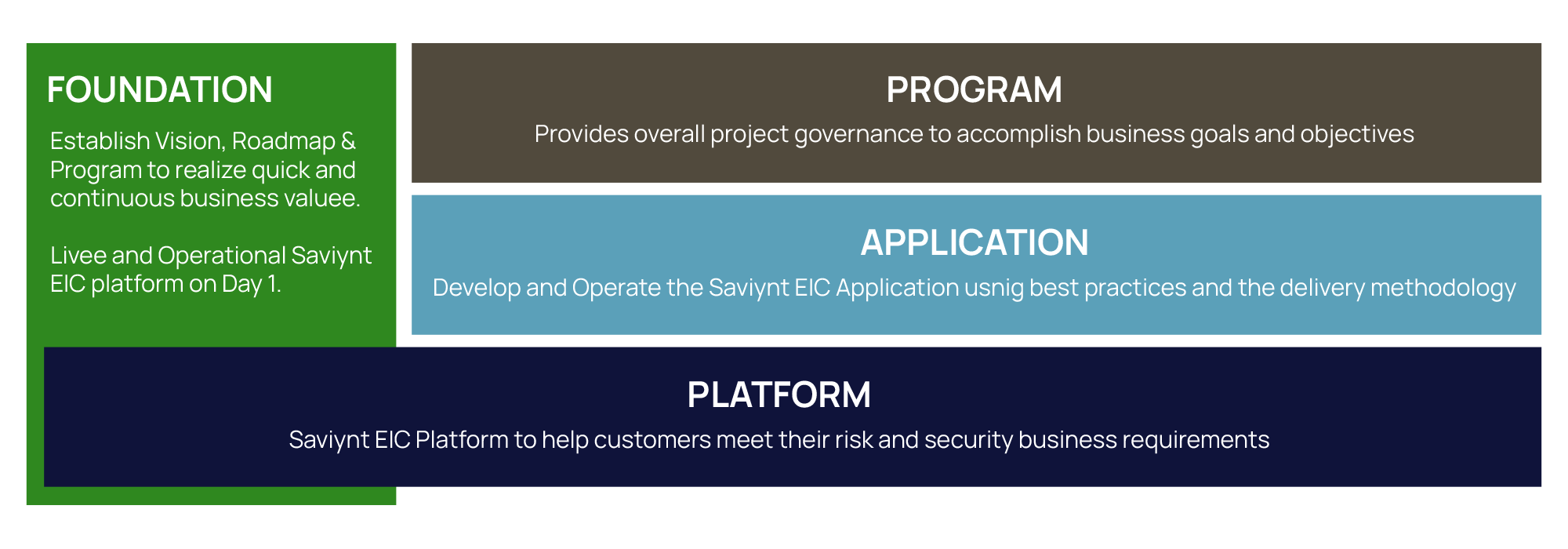
EIC Delivery Methodology Application
Application methodology follows a DevOps approach that integrates development and operations to streamline EIC delivery.
Our customers lead the industry in Identity Security Best Practices.

Ready to get started?
Contact us today.