
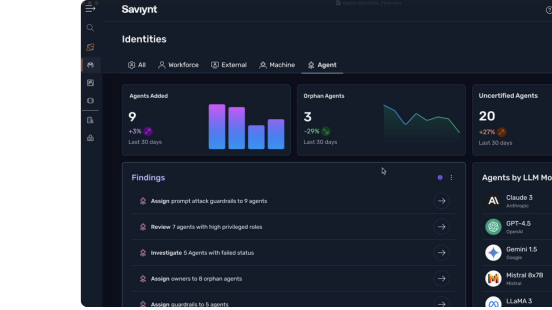
Get a comprehensive, real-time inventory of AI identity landscape.
AI agent discovery
Automatically discover agents and their associated identities — such as MCP servers and tools.
AI agent registration
Detect new added agents effortlessly and register them to the inventory in just a few clicks.
Learn how Saviynt is embracing and securing today’s AI landscape.

Proactively identify access risks and stay audit-readiness for all identities, including humans, machines, MCP servers, AI agents, and more.
-1.jpg?noresize&width=327&height=177&name=ISPM%20Main%20Dashboard%20Squared%20(2)-1.jpg)
.webp?noresize&width=1702&height=1174&name=uwa-bg%20(1).webp)
.jpg?noresize&width=2119&height=1415&name=iStock-1299972215%20copy%20(1).jpg)


An AI agent isn’t defined by a single identity — it’s composed of many. Each brings its own access patterns, lifecycle requirements, and security risks. These identities can consume sensitive data, initiate actions, and operate autonomously.
With AI, enterprises must now account for new classes of identities:
What makes Identity Security for AI Agents different from broader NHI security?
Although AI agents are technically part of the non-human identity group, their autonomous nature and ability to make independent decisions introduce a level of dynamism that traditional approaches can’t fully address. Securing them requires strategies that recognize their unique role bridging human and non-human identities. Unlike static service accounts, these agents continuously learn, adapt, and interact across complex infrastructure and intelligence layers—leaving conventional NHI tools, built for fixed and predictable entities, inadequate for managing their risks.