What is Privileged Access Management (PAM)?
What is Privileged Access Management?
Privileged Access Management (PAM) refers to the processes, systems, or technologies used to secure, manage, and monitor elevated access for human and machine identities. The principle of least privilege is a security strategy that restricts permission and access to resources to the minimum level required for each to do their job. Privileged users are particularly complex to manage because, as superusers or administrators, their level of access presents risks not applicable to typical roles.
Privileged Access Management systems are considered critical to the prevention and mitigation of both internal and external cyberattacks.
PAM: Privileged Access Management in the Workplace
It is not uncommon for organizations to have provisioned more privileged access than necessary. This is driven by increased IT complexity, including multiple cloud platforms and SaaS adoption by IT and other departments running “shadow IT.” These “shadow” systems are those deployed by other departments to work around the perceived shortcomings of the central information systems. Departments are continuously expanding their SaaS application use to meet customer demands. Many times, these apps bypass IT access control processes and InfoSec governance controls. Infrastructure is dynamic, with workloads created and terminated on an ad-hoc basis.
The digital transformation in organizations’ operating models increases the challenges that security and compliance teams face. Traditional privileged access management systems don’t provide visibility and governance at an appropriate scale to prevent privilege creep and reduce organizations’ overall risk.
Legacy PAM access management tools were designed to manage access to on-premises IT assets by storing credentials to shared accounts in a password vault, and then randomizing and rotating passwords to control access. One of the limitations of these privileged access management tools is that they do not discover escalated privileges stored on local devices. Another limitation of legacy privileged access management systems is that they were not designed with governance in mind. Therefore they require other tools or manual intervention to get monitor and audit privileged activity. All of this access management is complicated by today’s modern IT ecosystem. Organizations often choose numerous platforms for cloud security services, access management, privileged user access, and comprehensive governance capabilities. This leads to fragmented access management processes and inconsistent implementation of infosec policies. The inherent complexity and inconsistency of this approach is detrimental to an organization’s overall security posture.
Traditional PAM systems can’t keep up with cloud deployment architectures that are based on high availability, scalability, security, and business requirements. They are designed for more static environments and don’t have the flexibility to automatically identify changes in assets and resources as they get created or destroyed. Replicating this effort manually can waste significant work hours, translating to unnecessary costs and an overall higher total cost of ownership.
Privileged Access Management’s Business Impact
The transient nature of the cloud and the broad range of deployments — including hybrid, multi-cloud IT, and shadow IT setups — highlight the evolving challenge of enterprise resources. For example, when different environments have their own management and security paradigms, it’s challenging to get holistic visibility. This murky visibility coupled with the complex relationships between entitlements allows excessive access privileges to go unnoticed. As new resources or services are added, there is a chance of over-permissioning.
According to an IDC survey of CISOs in the US, 80% of respondents can’t identify excessive access to sensitive data in cloud environments. Two of the top three threats identified were lack of adequate visibility and permission errors. It’s impossible to fix the unknown. Organizations need advanced solutions to detect these misconfigurations and related vulnerability gaps in order to remediate them, ideally through automated, policy-based preventative controls.
An integrated approach to privileged access management should provide visibility, governance, and security in a single pane of glass. A PAM security solution like Saviynt’s Cloud PAM allow organizations to achieve frictionless identity and resource onboarding, as well as automated detection and remediation of misconfigured digital assets. Zero-Trust principles, applied to privileged access through an integrated, identity-led approach, provide organizations with a robust framework to improve their overall security posture.
.jpg?width=1824&height=1278&name=svt-modern-iga@2x%20(1).jpg)
Challenges of Privileged Access Management (PAM) in the Cloud Era
Organizations have identified that the traditional vendor approach to Privileged Access Management (PAM) doesn’t meet the current needs of today’s enterprise. Traditional access management solutions lack comprehensive oversight and require expensive deployment and operational costs. And considering how DevOps pipelines and SaaS adoption are expanding, legacy access management solutions quickly start to lose their overall value. Organizations need an agile solution that keeps pace with their business, while simultaneously balancing the security needs of an ever-changing business environment.
PAM solutions for access management work by collecting privileged accounts’ credentials into a secure repository, lowering the risk of admin credentials being stolen by outsiders or misused by insiders. Legacy tools grant privileged users access to “walled off” resources using these credentials via VPN tunnels. For on-premises resources, this model works just fine.
This model doesn’t support doing business in the cloud for several reasons. For one, cloud resources are continually scaling up and down, and legacy PAM solutions don’t offer matching flexibility. They scan environments at regular intervals, and those intervals don’t match the rate at which cloud resources auto-scale, leaving them periodically unmonitored.
Additionally, the cloud’s flexible nature creates risk when organizations rely on a legacy PAM strategy of persistent operating system accounts with static permissions. Credentials with standing privilege, such as administrators and superusers, become more vulnerable because workloads and resources are continually shifting. Users end up with access to resources they no longer need, and credentials sit around for long periods, vulnerable to attack.
Read 5 Reasons Lifting-and-Shifting Legacy PAM to the Cloud Doesn’t Work to learn more about the insufficiency of legacy PAM tools for securing cloud resources.
Saviynt & Cloud Privileged Access Management (Cloud PAM)
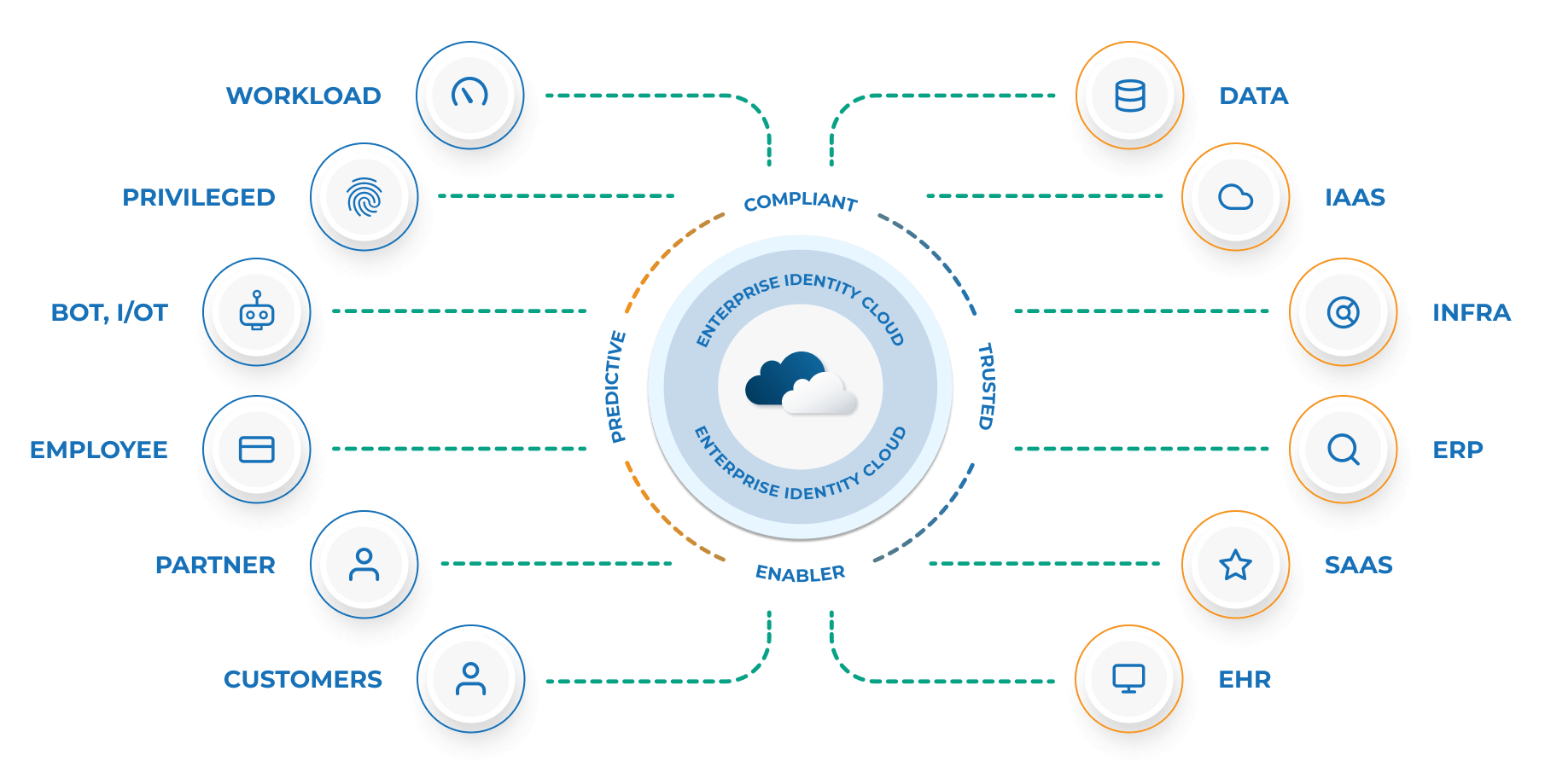
In 2021, Saviynt introduced an innovative PAM solution within our Identity Cloud. It’s cloud-native, secure (FedRAMP certified), and utilizes a converged platform to deliver identity-based Privileged Access Management services. Identity Cloud forms the foundation for organizations implementing Zero-Trust architecture by enabling visibility, management, and privileged access monitoring. Augmenting this with just-in-time (JIT) provisioning of accounts with zero standing privileges that are time-bound — and automatically revoked — reduces organizational risk.
Saviynt Enterprise Identity Cloud consistently applies governance, compliance, and security rules throughout the cloud and on-prem ecosystem. This is important when providing evidence and demonstrating continuous compliance in the audit process.
The intuitive, wizard-based onboarding interface makes application integration easy and efficient. Auto-discovery and rapid enrollment of cloud workloads accelerate cloud service integration which in turn helps companies securely operate in the cloud.
Oversight of the full identity lifecycle with access governance, Segregation of Duties (SoD) risk evaluation, privileged access management, and risk-based access certification is centralized in a single platform. Such centralization creates a consistent user experience for all personas through a single-pane-of-glass interface. This reduces the strain of splitting focus between multiple point solution interfaces, increasing effectiveness, and saving time.
Saviynt’s integrated approach creates a comprehensive solution for cloud security by merging IGA, CPAM, and CIEM. Not only does it provide visibility and privileged access management, but it also includes:
-
Automated entitlement discovery
-
Entitlement relationship visibility
-
Policy-driven management of privileges
-
Just-in-time access provisioning with automated revocation
-
Monitoring and reporting of privileged access usage
-
Remediation of excessive privileges
Instead of relying on point solutions, customers get a single platform to improve their cloud security and compliance posture continuously. Customers like Equifax have reduced their risk footprint by enabling Saviynt CPAM capabilities in as little as three months and have quickly benefitted from the results.
Resources


