.png?noresize&width=981&height=729&name=Untitled%20(435%20x%20363%20px).png)
.png?noresize&width=435&height=363&name=Untitled%20(435%20x%20363%20px).png)
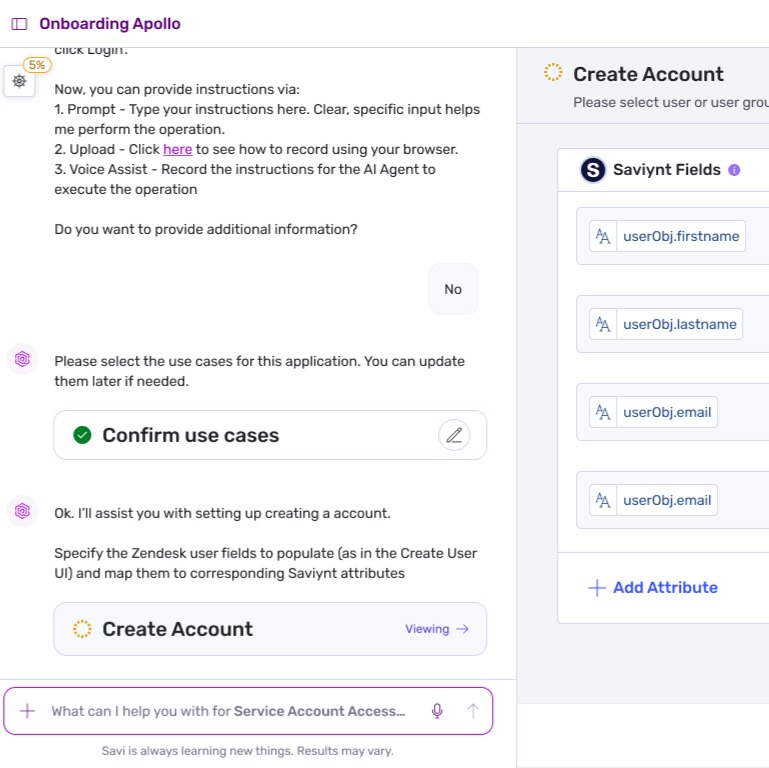
Gain real-time, fine-grained insights into access and entitlements for apps like SAP and Oracle using advanced analytics dashboards.
Application access dashboard
Automatically discover and visualize fine-grained access and entitlements across your application ecosystem for comprehensive transparency.
Entitlement analysis view
Drill into detailed entitlements with customizable filters, sort by app type, risk level, ownership, and more for targeted insights.
Risk visualization interface
View and prioritize access risks in real time, analyzing potential violations with graphical trends and audit-ready reports.
.png?noresize&width=327&height=177&name=AAG%20-%20Fine%20Grain%20Visibility%20-%20Entitlements%20-%20Square%20(1).png)
Identify SoD violations instantly using pre-configured, app-specific rulesets for SAP, Workday, and Oracle, streamlining compliance enforcement.
SoD rules dashboard
Automatically apply pre-built SoD rulesets to detect violations across apps, helping you instantly visualize compliance status.
Violation analysis interface
Review and prioritize SoD violations with filters for app type, risk severity, and user roles, enabling rapid compliance checks.
Ruleset configuration portal
Customize and deploy app-specific SoD rules for Oracle and Salesforce, ensuring automated enforcement with minimal setup effort.

Leverage AI-driven analytics to detect and prioritize access risks across applications, enabling proactive fraud and violation prevention.
Risk prioritization dashboard
Visualize and prioritize access risks in real-time using AI-driven insights across apps, ensuring proactive compliance monitoring.
Anomaly detection interface
Analyze anomalies with AI-powered filters, sorting risks by severity and app type to prevent violations and fraud.
Predictive risk scoring portal
Generate predictive risk scores for access requests, enabling preemptive prevention of SoD violations and fraud, with automated alerts.

Automate access reviews with intelligent certification workflows, ensuring compliance for apps like Salesforce with minimal manual effort.
Certification campaign manager
Launch automated access certification campaigns for apps like Salesforce, streamlining entitlement reviews with pre-configured compliance workflows.
Access review dashboard
Monitor and validate app entitlements in real-time, using intuitive dashboards to ensure compliance with minimal administrative overhead.
Approval workflow interface
Customize and approve access certifications with role-based workflows, ensuring rapid, compliant entitlement validation across critical applications.

Grant secure, temporary access with automated session monitoring and revocation, protecting critical apps from unauthorized use risks.
Emergency app access console
Quickly provision temporary access for critical apps like SAP, with automated monitoring to ensure secure, compliant usage.
Session tracking dashboard
Monitor emergency access sessions in real-time, visualizing activity across apps to prevent unauthorized access and ensure compliance.
Access revocation workflow
Automate revocation of temporary access with pre-configured workflows, securing apps like Oracle against misuse and audit risks.
.png?noresize&width=327&height=177&name=AAG%20-%20Emergency%20Access%20-%20Square%20(1).png)
Streamline audits and reduce costs by automating compliance and identifying unused access across cloud and on-premises apps.
Compliance audit portal
Automate compliance audits for GDPR and SOX, generating reports to ensure regulatory adherence with minimal effort.
License optimization dashboard
Identify and eliminate unused app access to optimize license costs, visualizing savings across SAP and Workday.
Cost analysis workflow
Analyze access usage with automated workflows, reducing compliance costs and ensuring efficient governance for critical apps.
.png?noresize&width=327&height=177&name=AAG%20-%20Compliance%20and%20Cost%20Optimization%20-%20License%20Optimization%20-%20Square%20(1).png)
Explore today’s business application environment and an analyst review of the unique capabilities and benefits that Saviynt provides.